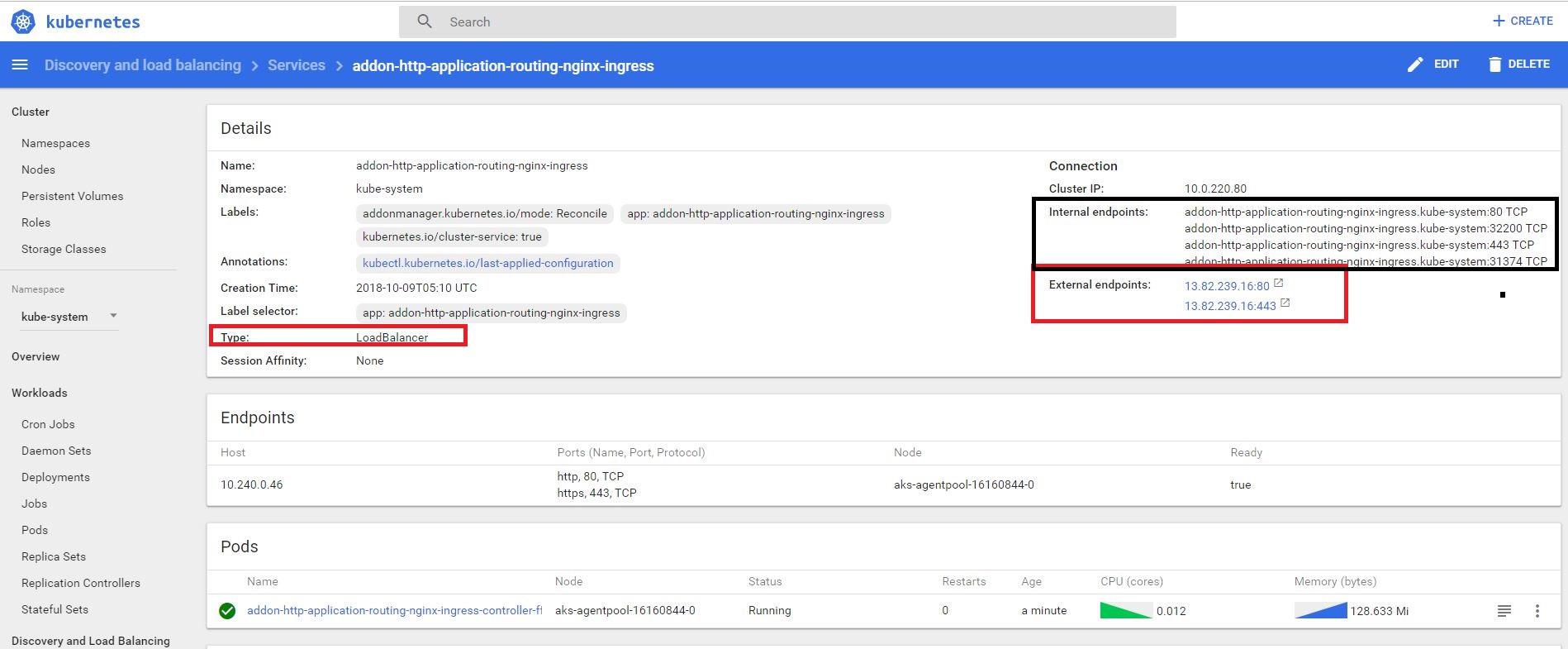
When I initially created the aks cluster in Azure, I did not pay attention to the question on the wizard and it created something called HTTP application routing. It’s a nightmare for security professional! It creates a service with a load balancer in kube-system with a public/external ip and it creates couple of NSG rules in the same subnet where your aks nodes are attached!
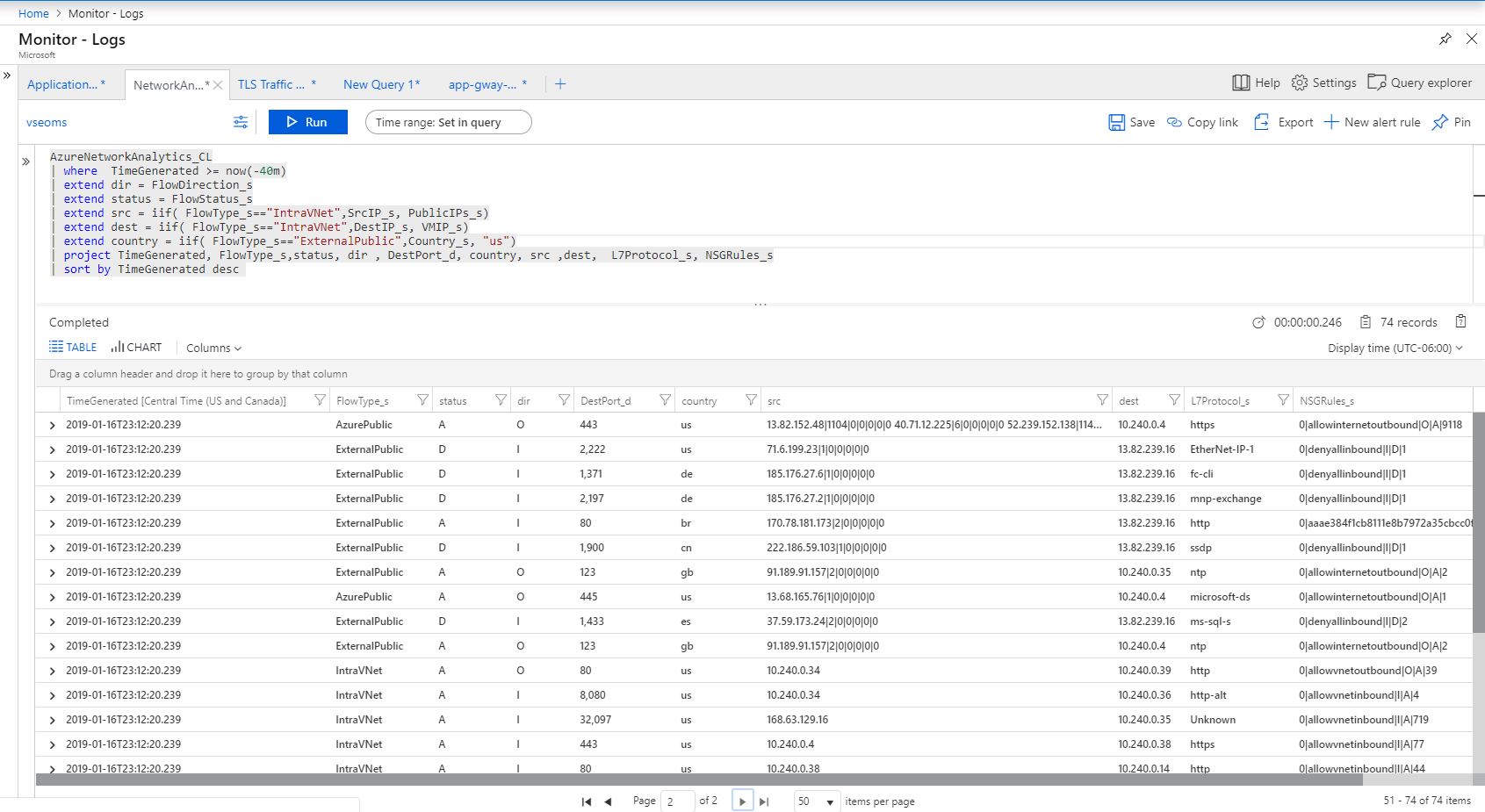
So, what’s the problem? Bad actors all around the world enumerate Azure public ip and get into your private subnet over port 80/443. This is possible because of the auto generated nsg rules to allow any/any traffic! If you update those rules to block/filter traffic to public ip, they will be recreated by Azure when you restart or stop/start the aks nodes! It’s like a cat and mouse game! Following image shows updated rules but they will be changed to allow traffic from Internet.
Microsoft already cautioned people not to use it in production. Why introducing it in non-prod to begin with?
Caution: The HTTP application routing add-on is designed to let you quickly create an ingress controller and access your applications. This add-on is not recommended for production use. For production-ready ingress deployments that include multiple replicas and TLS support, see Create an HTTPS ingress controller.
If you happen to have it in your production AKS, simply remove it. You can run the below command in Azure Cli, be sure to change the name and group.
az aks disable-addons –addons http_application_routing –name myAKSCluster –resource-group myResourceGroup –no-wait
Bad actors are continuously trying to get into your systems and they may utilize this vulnerability in aks. I could see people from across the world were trying to get to my aks nodes but they were denied since I changed those auto generated rules.
Once I figured out Azure is overwriting my rules on restart or stop/start of nodes. Azure even recreated the public load balancer as well as the rules! I had enough and simply removed the HTTP application routing for good.
Note: A DNS zone is tied to http application routing add-on. If you remove the add-on, dns zone will be removed automatically. Your private dns record tied to Kubernetes service will no longer work!