It’s been couple of months since I started security automation to stop the bad actors at the front gate and stop them from probing web sites deployed in Azure App Services. Feel free to read my previous post, Security Automation based on Actionable Intelligence (AI), if you missed it. In this post, we would like to discover if the design is working. Solution design can be changes to support multi-tenant architecture and it can be a commercial SaaS/PaaS service. Let’s look at the logical design and automation flow-
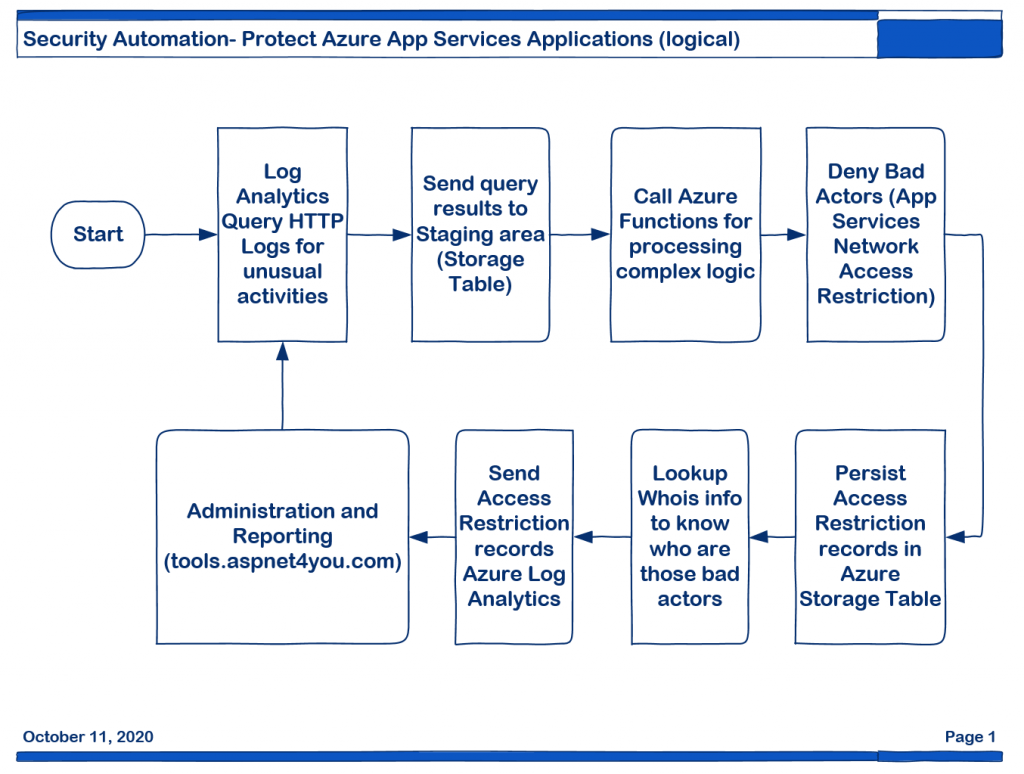
As mentioned in the previous post, we are using Azure Logic App to auto schedule the job and use logic app as the starting point. Yes, logic app can do lot of tasks but when it comes to complex operation you have to rollup the sleeves and write your own codes! There are so many choices but one of our objective is to keep the cost down. Welcome to Azure Function- the serverless. AddUpdateAccessRestriction Azure Function is being called after data is staged in a table.
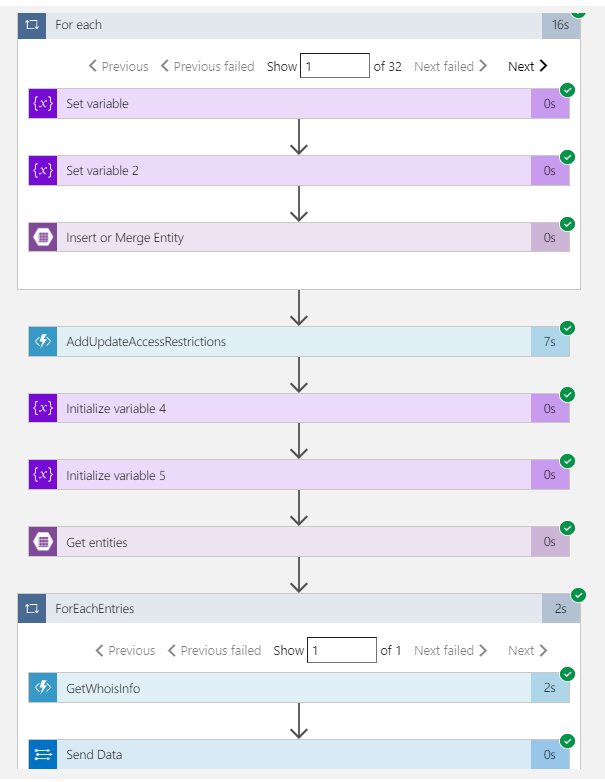
AddUpdateAccessRestriction Azure Function is adding deny rule at web application network restriction.
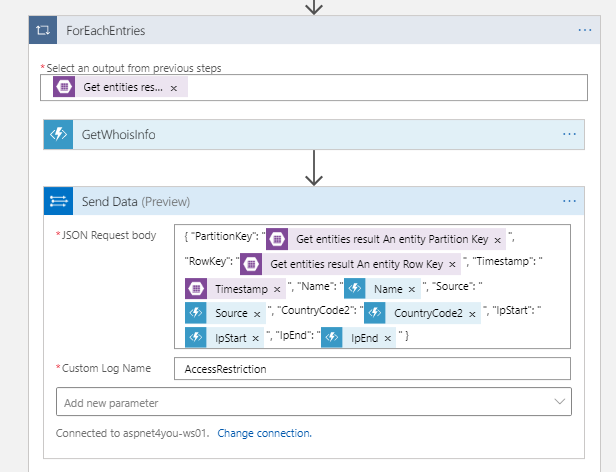
Tools at Aspnet4you comes with Whois search and it brings lot more details. We needed a light version of whois to show who are those bad actors for reporting. I had to create a new function GetWhoisInfo to find the owner of the ip address. Quick lesson learned, Logic App can’t see Azure Functions with custom route. I had to remove the custom route and pass the input parameter in request body!
Logic app is cool and Microsoft is continuously adding more features. One such feature is ability to send custom data to log analytics workspace. Log analytics Send Data is in preview but it works. Why brining this data into log analytics? One of the reason is, we have other logs in the workspace and we can easily join tables for reporting purpose. Having data in log analytics allow us to conduct further analysis and tune the access restriction rules.
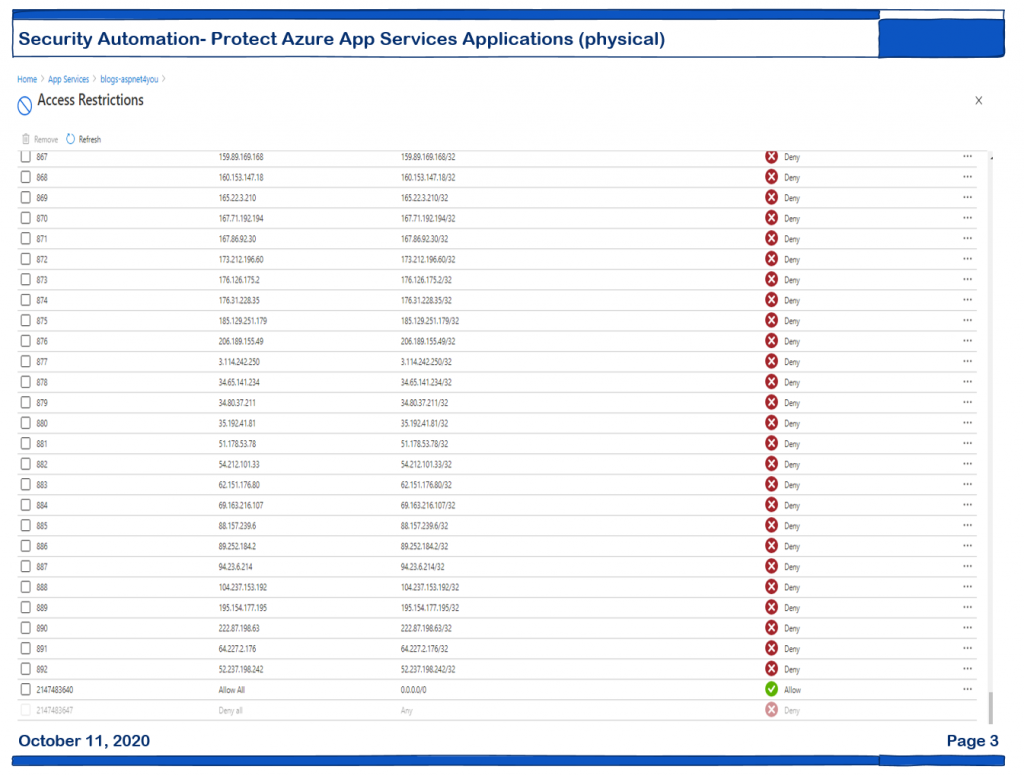
Okay, our automation is in action. Let’s see who are those actors messing up with our apps for no apparent business reason. You can find them at Tools at Aspnet4you but here is a sample screenshot-
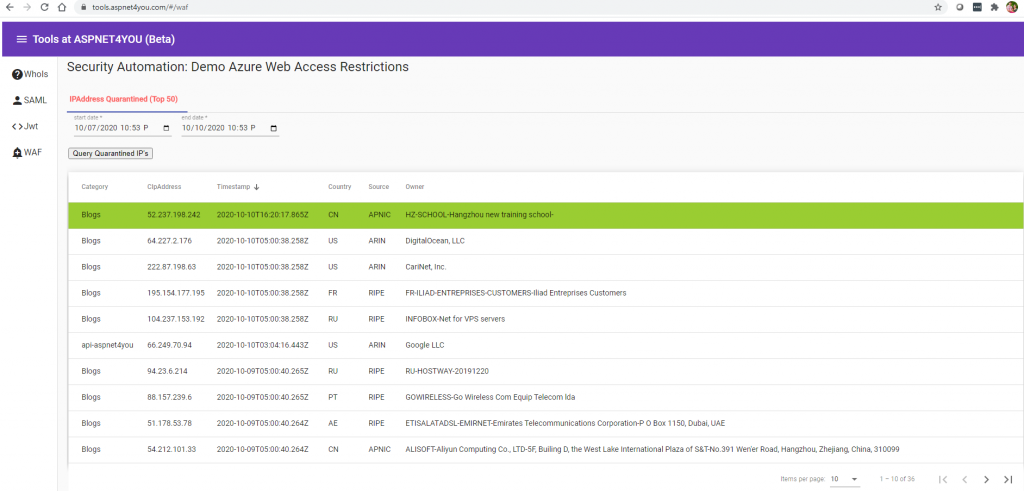
You can click one of those ip address and see what they were doing in the application. Why they are coming after wordpress login or xmlrpc so many times? Another interesting lesson is, zero trust- you can’t trust anyone including reputable cloud providers (Azure, AWS and Google) because those crooks are often resident of public clouds!
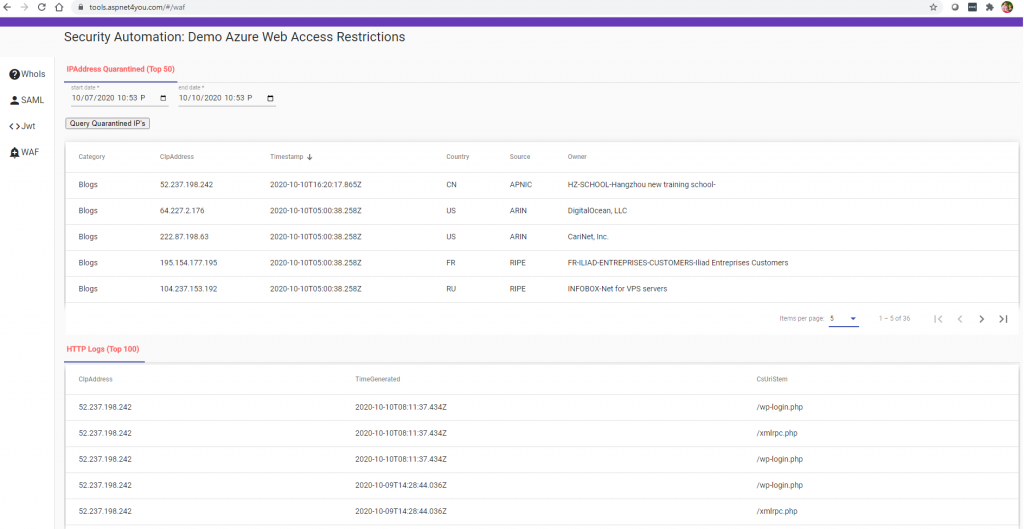
Conclusion: You can build security automation like this in Azure or in other cloud. Data is at the heart of the solution, data is gold if we use them appropriately. Some companies are very good in collecting logs and they are pushing those logs into their choice of SIEM. However, they don’t spend enough capital to analyze the data and make them useful.
