Are you O365 Administrator or InfoSec Architect? You may be interested to read this post. Some organizations don’t allow guest access to their O365/Azure tenant due to fear of exposure of internal data or due to lack of proper security controls. Let’s explore how to enable our business by allowing guest users into O365/Azure tenant with adequate safeguards. I think it’s best to draw the high level requirements-
- Automated onboarding and offboarding of guest users in O365/Azure tenant.
- At least one level of approval is required before guest user can be approved.
- Auto disable guest user after N days.
- Access Review of guest users every month or quarter.
- Guest user must comply with multi-factor authentication (MFA).
- Guest user can’t have access to Files under Teams Channels. Those files are stored in SharePoint site mapped to the Team or OneDrive of user. Guest must not have access to those underlying SharePoint or OneDrive.
- Guest user can chat and participate in meetings but they can’t download anything shared in chat. This is required for DLP control.
- Guest user can share or present screen in team meetings.
- Don’t allow users (any type) to download, copy/paste contents from MS Teams mobile app to user’s personal space on their BYOD device. DLP control to prevent data exfiltration (optional for the story).
- Retain audit logs for 365 days.
Okay, we have our requirements and we need to decide what tools or services can be used to satisfy the requirements. Thanks to Microsoft, we can use Azure/O365 Native services to implement or configure settings. Services to be used –
- Azure/O365 Directory. You need a house to have party and invite guests!
- Azure Identity Governance to implement automatic onboarding, offboarding, approval and access review.
- Azure Conditional Access policy with MFA (native) for Guests and External Users.
- M365 Admin Center to control settings in Teams Admin and SharePoint Admin.
- MS Teams client (Mobile App and/or Web Browser) for testing controls.
- Intune device policy to control what user can and can’t do in MS Teams native app (optional for this story).
- Azure Log Analytics to store and retain audit logs.
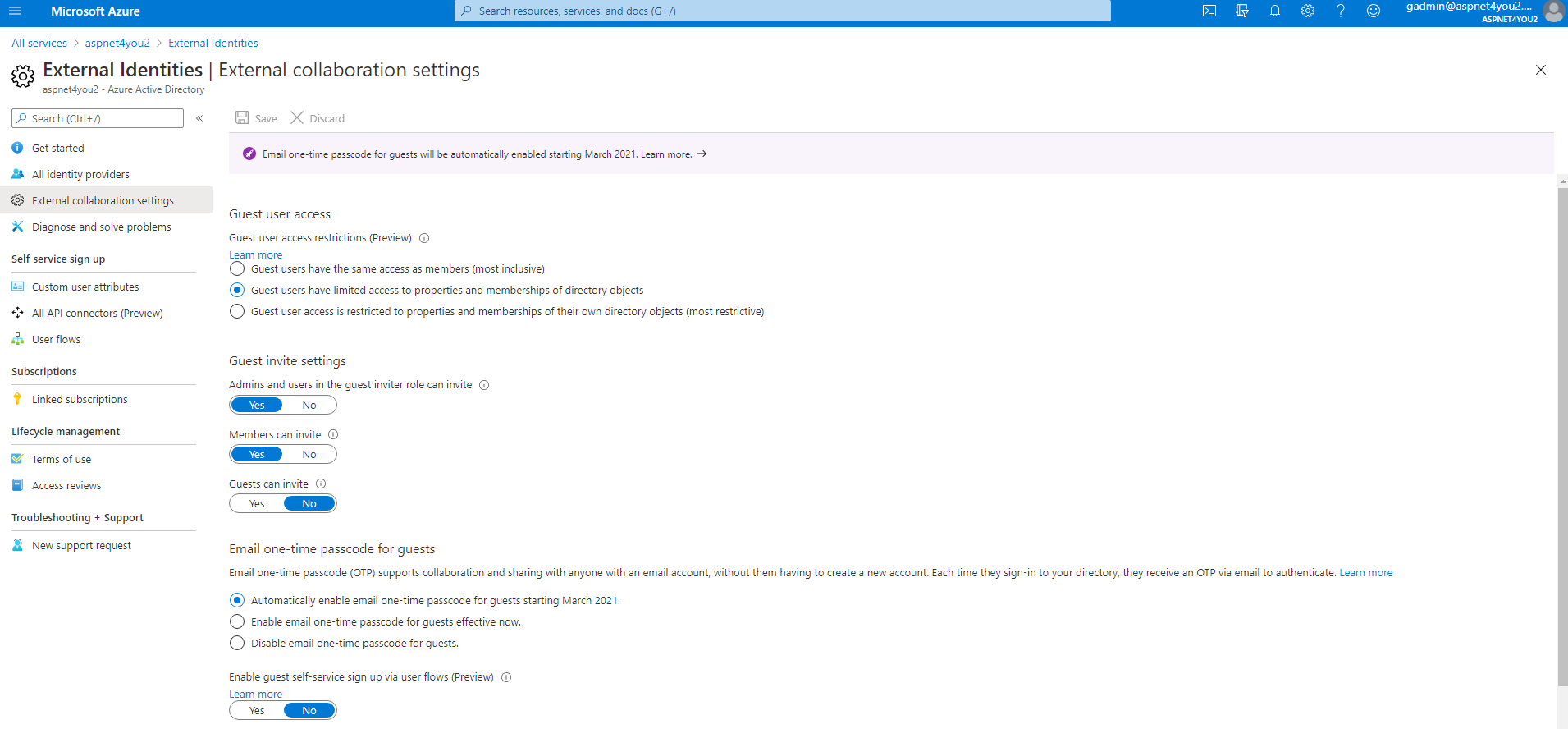
Let’s configure External collaboration settings at the Azure Active Directory. You can adjust the options based on the level of risk that you are willing to accept.
Configure guest access in Teams lets people outside your organization access teams and channels. This is done at Org-wide settings > guest access section on admin.teams.microsoft.com. Allow guest access in Teams need to be ON. This will bring additional control options and you can turn on/off each settings based on your detail requirements.
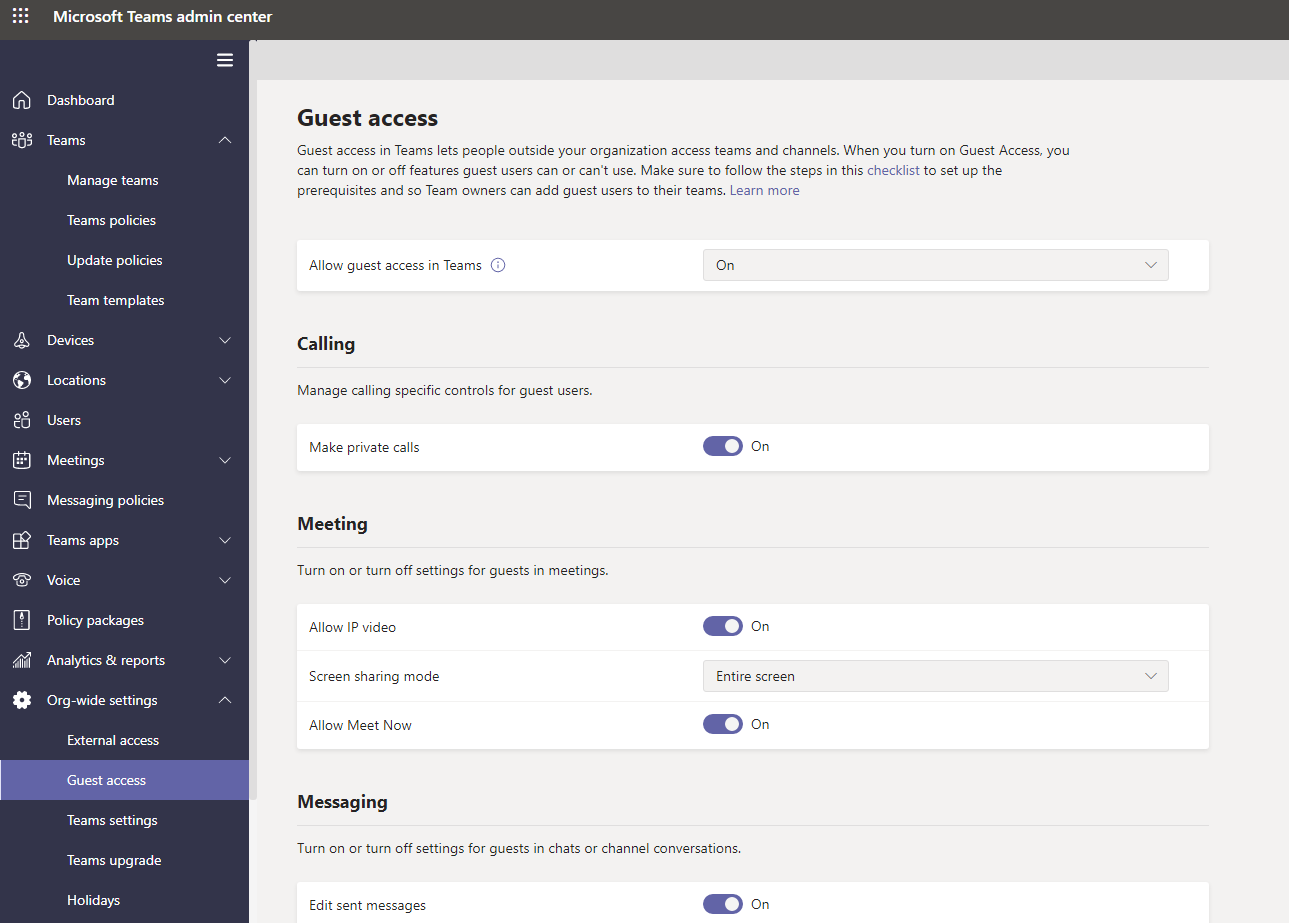
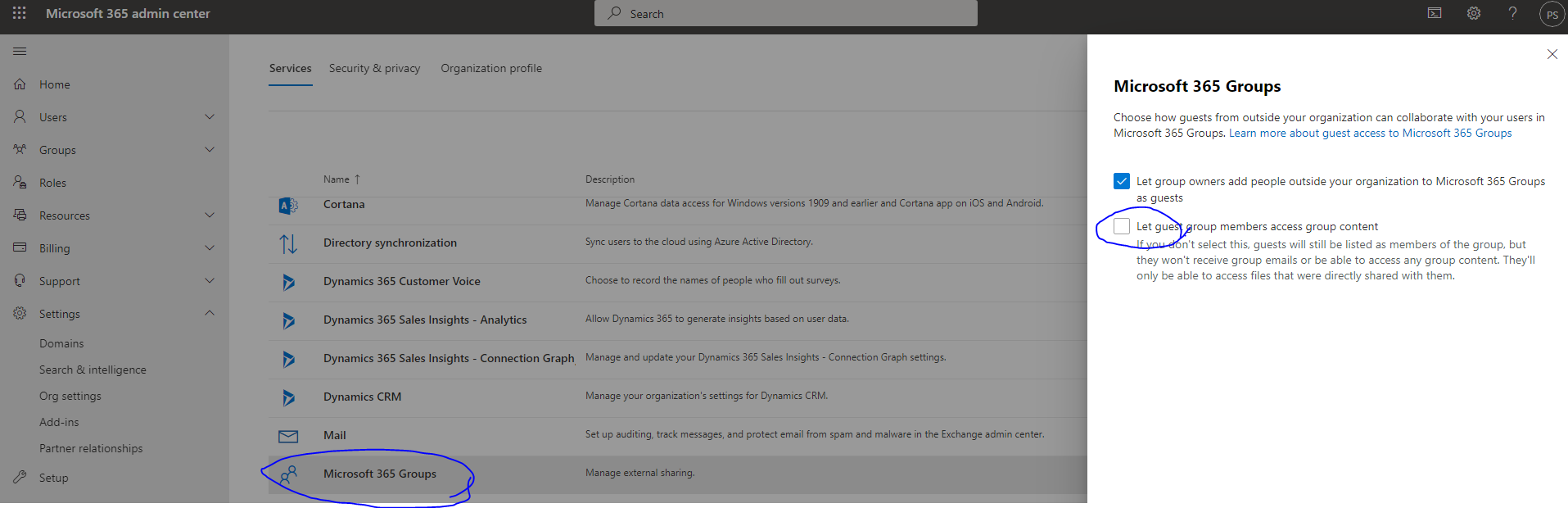
We don’t want the guest to access files from SharePoint/OneDrive. Guest will not see/view files when they login to MS Teams app. This setting is controlled at M365 Admin Center. Go to Settings > Org settings > Microsoft 365 Groups and uncheck “let guest group members access group content”.
Configure Azure Conditional Access policy to enforce MFA for guest and external users. Don’t worry, you don’t have to register any device. Microsoft will ask guest user to enter their phone number where one-time code would be delivered. Optionally, a separate CA policy can be used to force guest users to use Azure MCAS proxy to control browser session – when web browser is used as client. See Protect apps with Microsoft Cloud App Security Conditional Access App Control for more info.
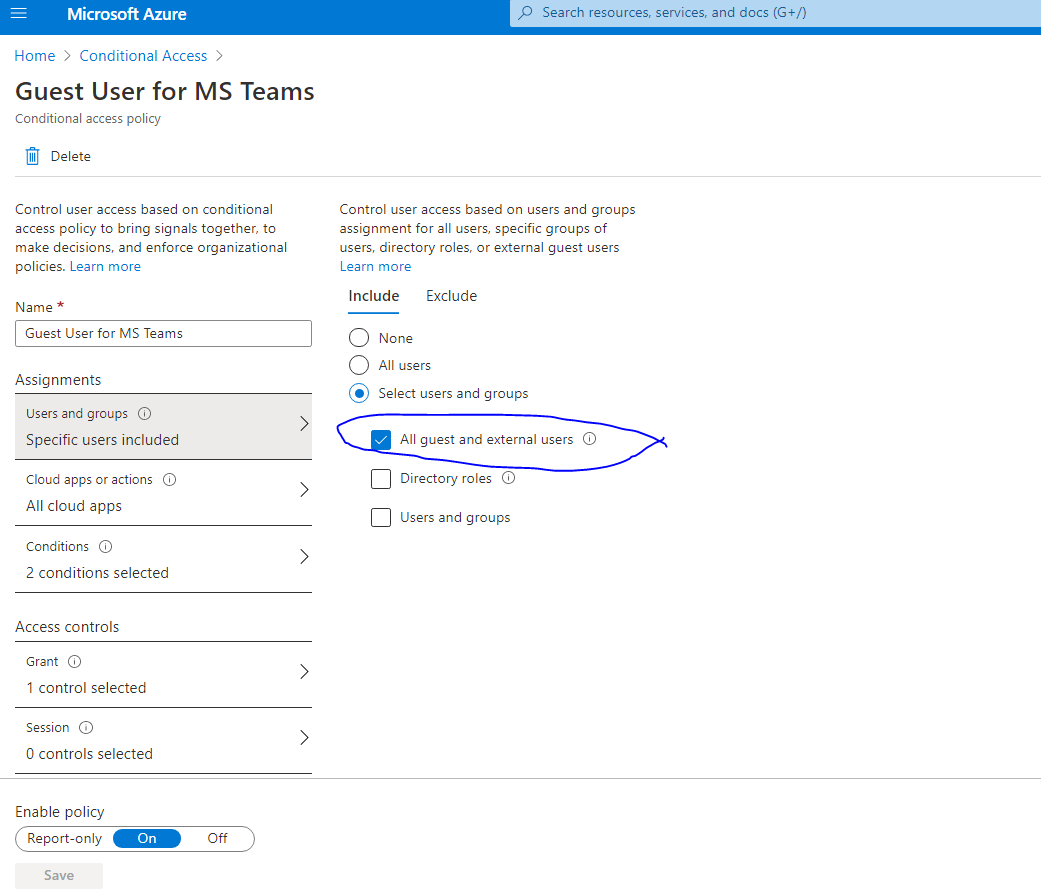
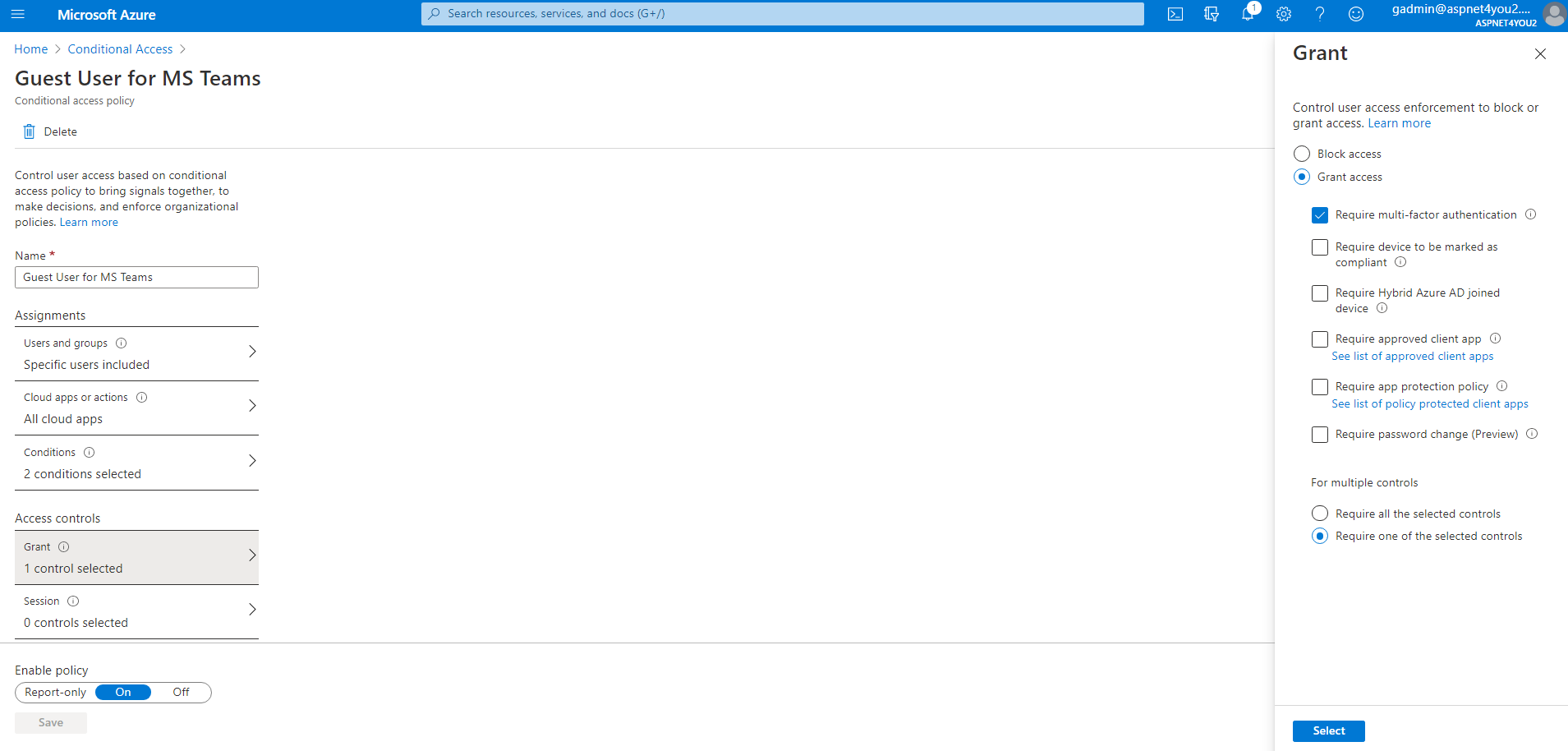
Now, let’s focus on Azure Identity Governance to automate guest user onboarding/offboarding. We will configure the following in Identity Governance –
- Create a Catalog.
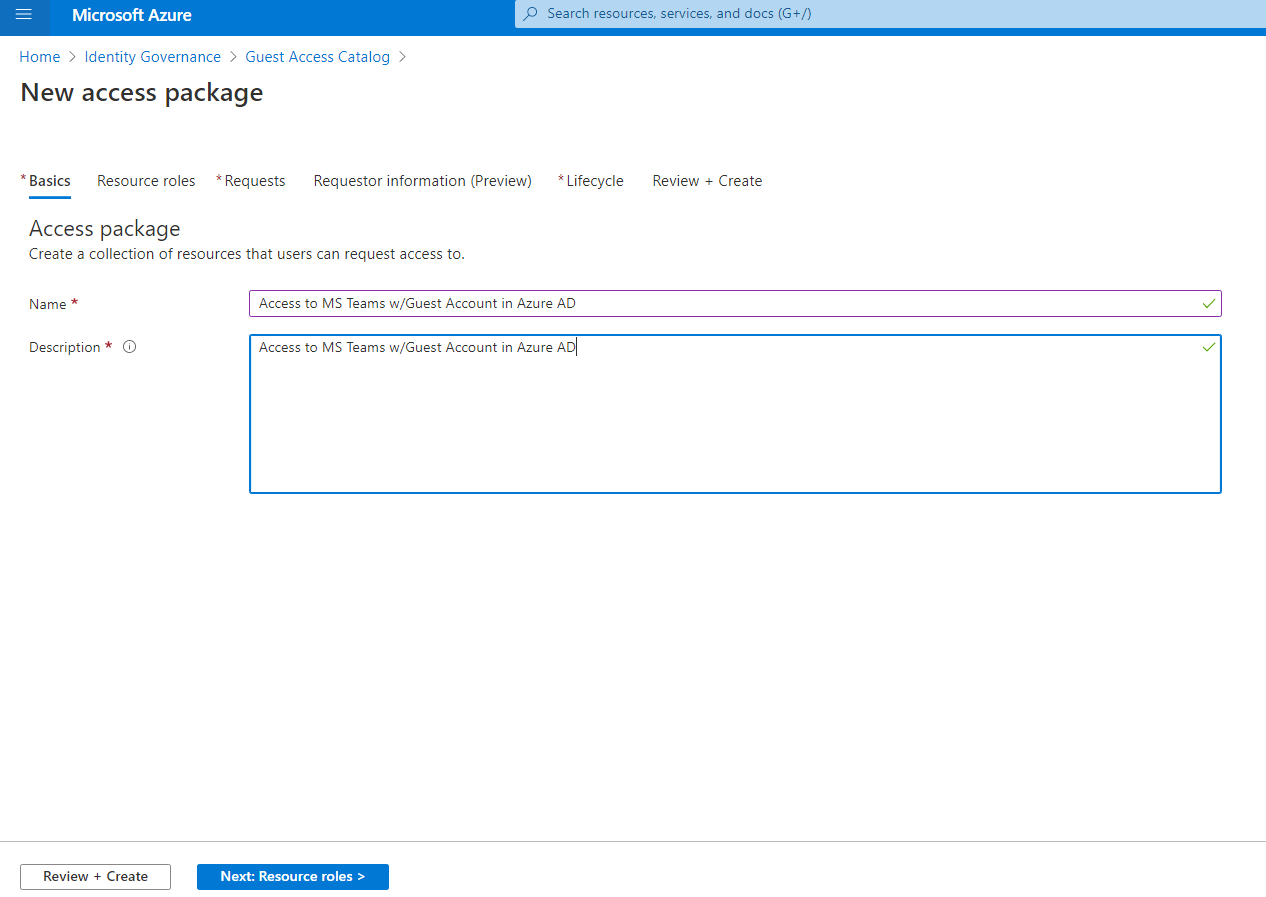
- Create an Access Package with a Policy. Assign resource roles, you can add MS Teams if you would like guest user to be part of the team. Guest user will become member of this group once approval is complete.
Create Catalog, Enabled and Enabled for guest access-
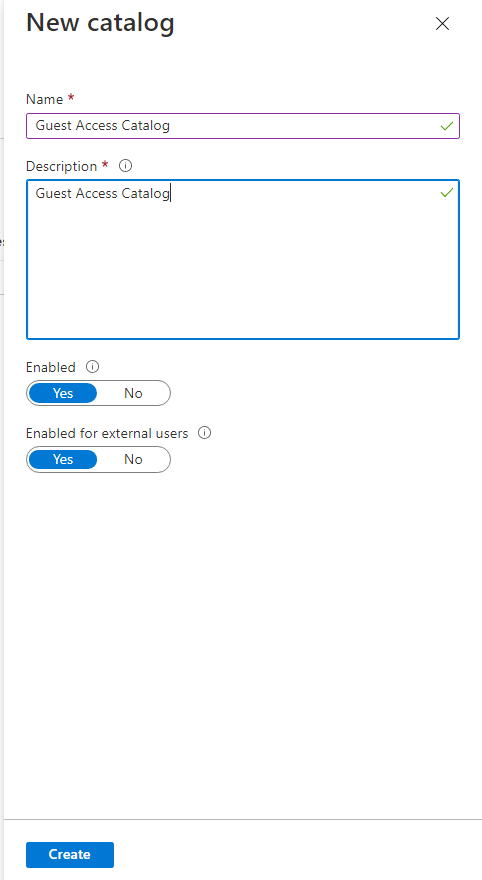
Create a new Access Package –
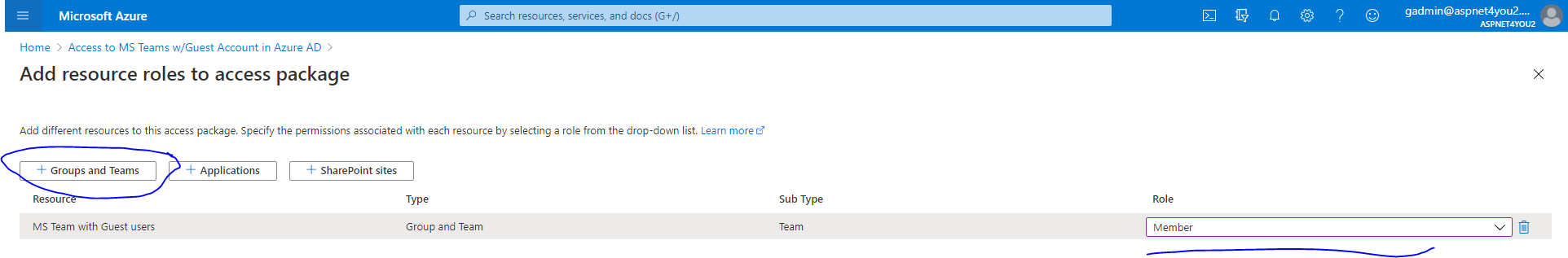
Add resources role to the package. We will add “MS Team with Guest users” team under Groups and Teams and role as Member. Don’t forget to click the Add button at the bottom!
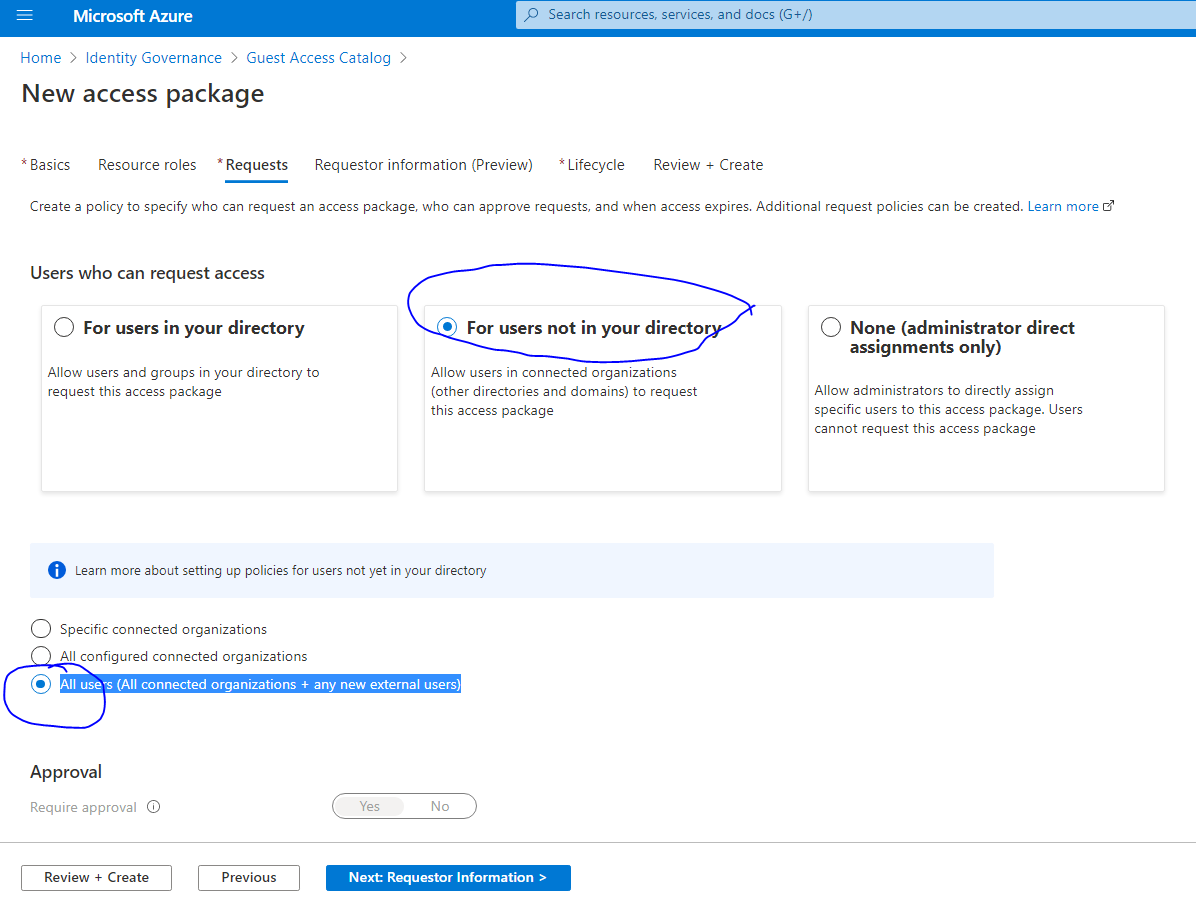
Configure Request tab. Select “For users not in your directory”. Select option All users (All connected organizations + any new external users). We are going to configure one level of approver but you can select up to 2 levels of approval. Approval levels are sequential.
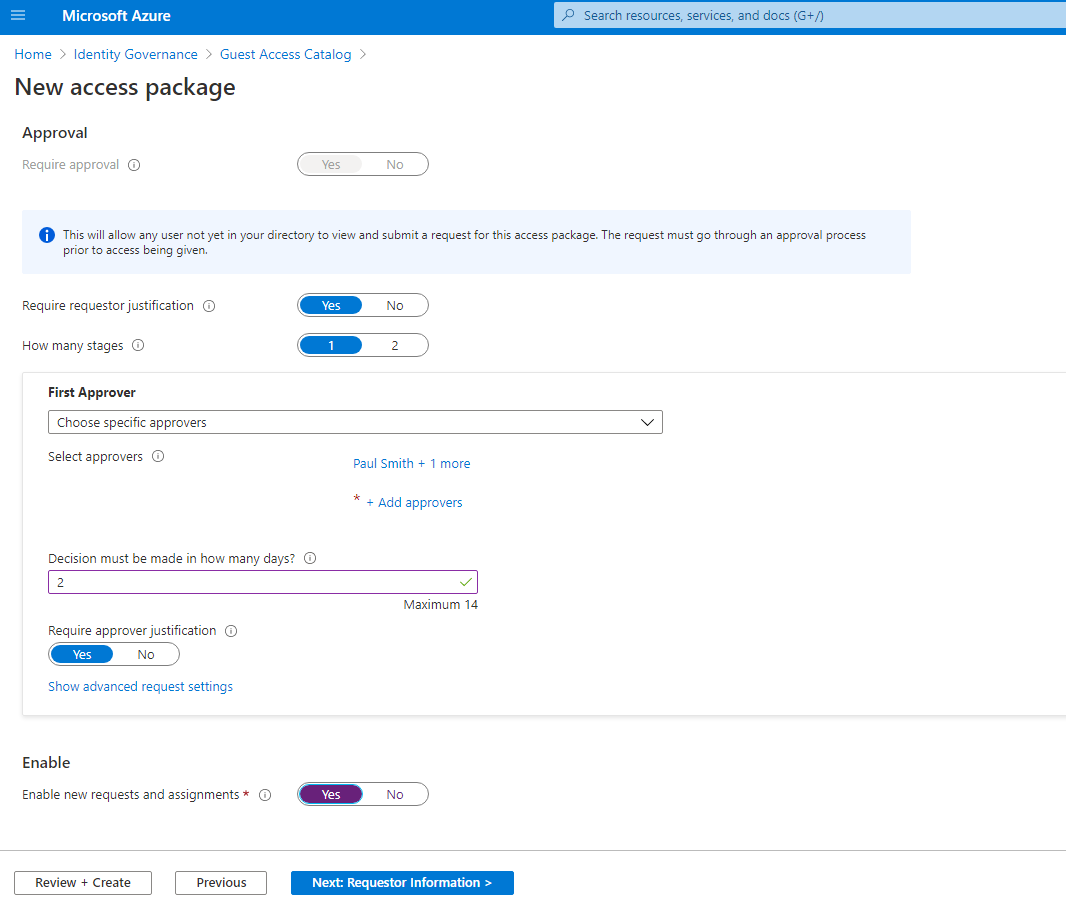
Add Requestor Information. This is where you add legal disclosure, any instructions, signature, etc. that you would like to collect when user submits a request for access.
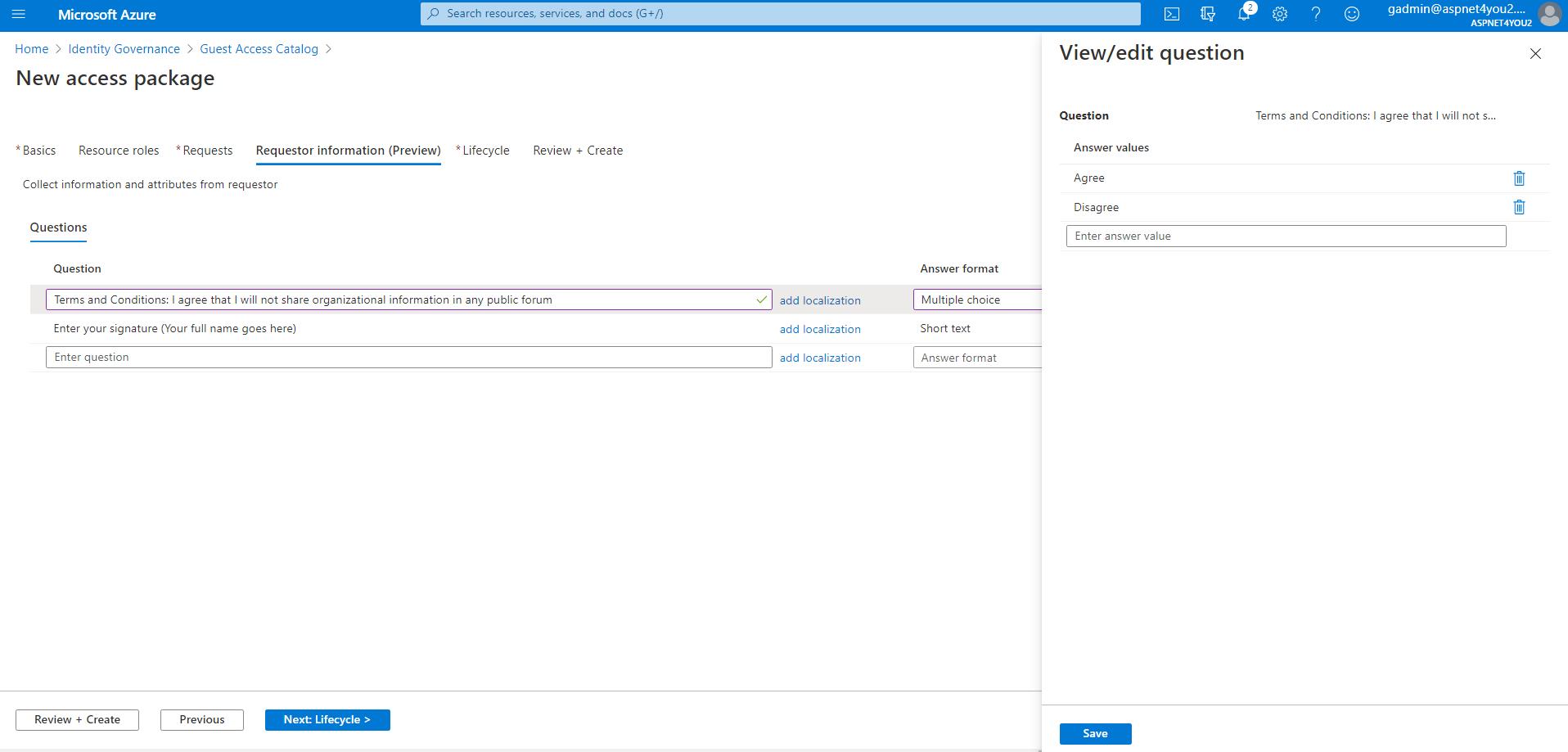
Configure Lifecycle- specify when access or assignment expires, if access review required and person or group responsible for access review.
Okay, we have all the components in the catalog – access package, resource assignment, policy that is part of access package.
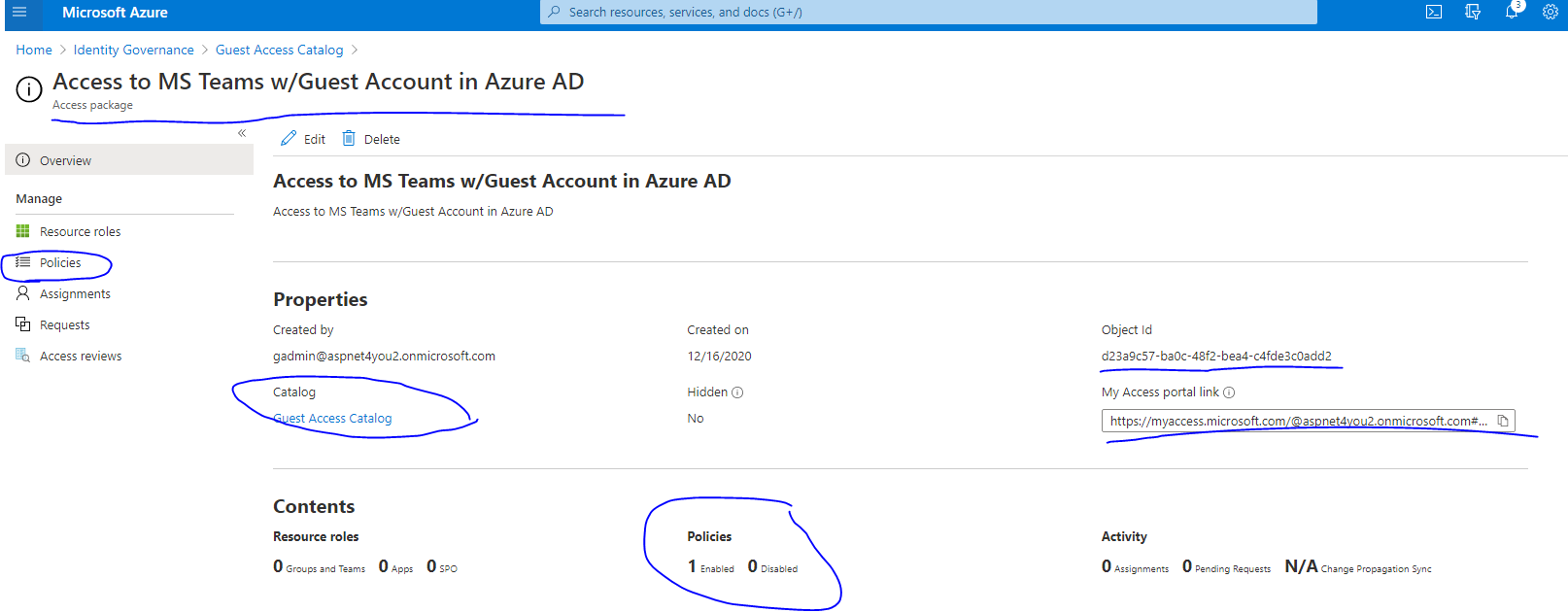
We are now ready to send invites to guest and the URL link is available at the access package overview page. URL format: myaccess.microsoft.com/tenant-name/access-package-id. (example: https://myaccess.microsoft.com/@aspnet4you2.onmicrosoft.com#/access-packages/d23a9c57-ba0c-48f2-bea4-c4fde3c0add2).
Testing, Testing and Testing! Here is our testing strategy-
- One outlook.com personal account
- One aspnet4you.com external domain/partner. Notice- this domain is different from aspnet4you2!
- Two gmail.com personal accounts. Note that Microsoft will not allow non-Microsoft account to sign-in to Azure AD. Gmail account is required to register with Microsoft. We will use the 2nd gmail.com account to test sign-in failure.
- Verify guest user can’t access files or download/upload files.
- Verify guest user can send and receive messages.
- Verify guest user can join meetings.
- Verify guest user can share or present screens at the meetings.
- Accounts to be used –
- MSTeamTest001@outlook.com
- MSTeamTest001@aspnet4you.com
- MSTeamTest001@gmail.com
- MSTeamTest002@gmail.com
- Paul.Smith@aspnet4you2.onmicrosoft.com is the owner of ” MS Team with Guest users” team and Paul will have full access to team channels.
- Paul Smith happened to be the approver in Identity Governance. He would have to approve the guest access requests.
- MS Teams app on Desktop.
- MS Teams app on Mobile.
Paul Smith sign-in to MS Team App on Windows 10 desktop and Paul can see/do everything. This is expected since Paul is the owner of the team and he is a member of the organization.
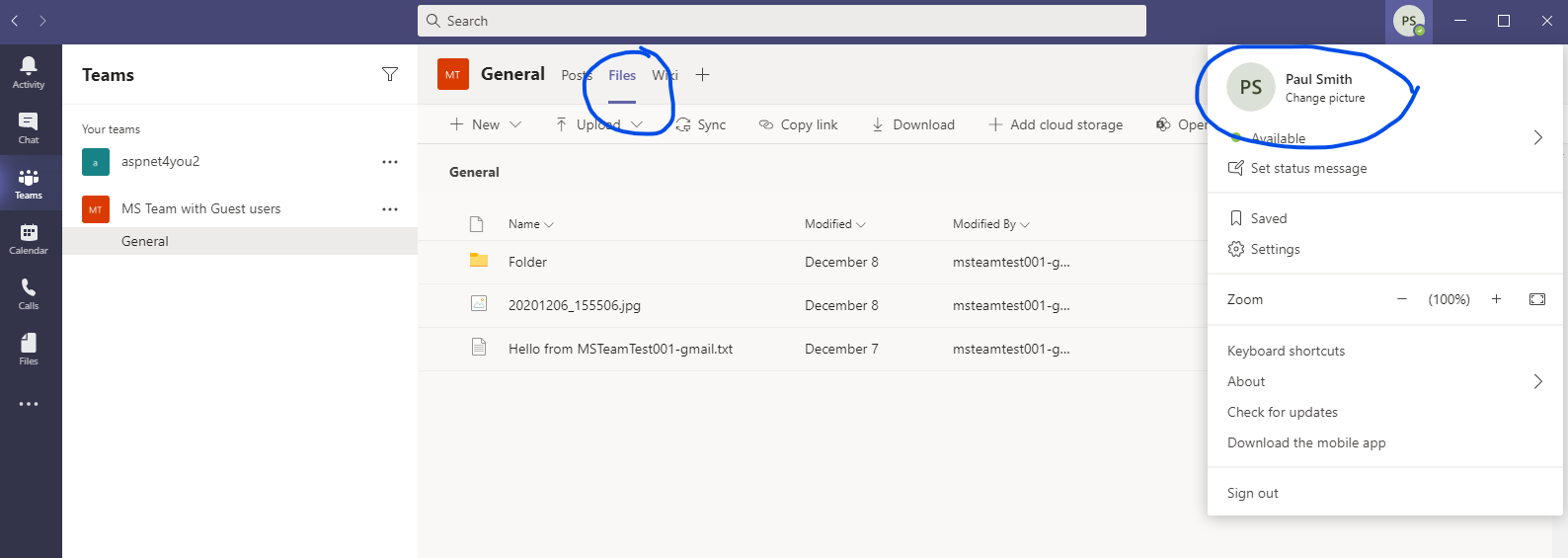
Paul can see/add members, add/modify team channel since he is the owner of the team. No guest user at this time.
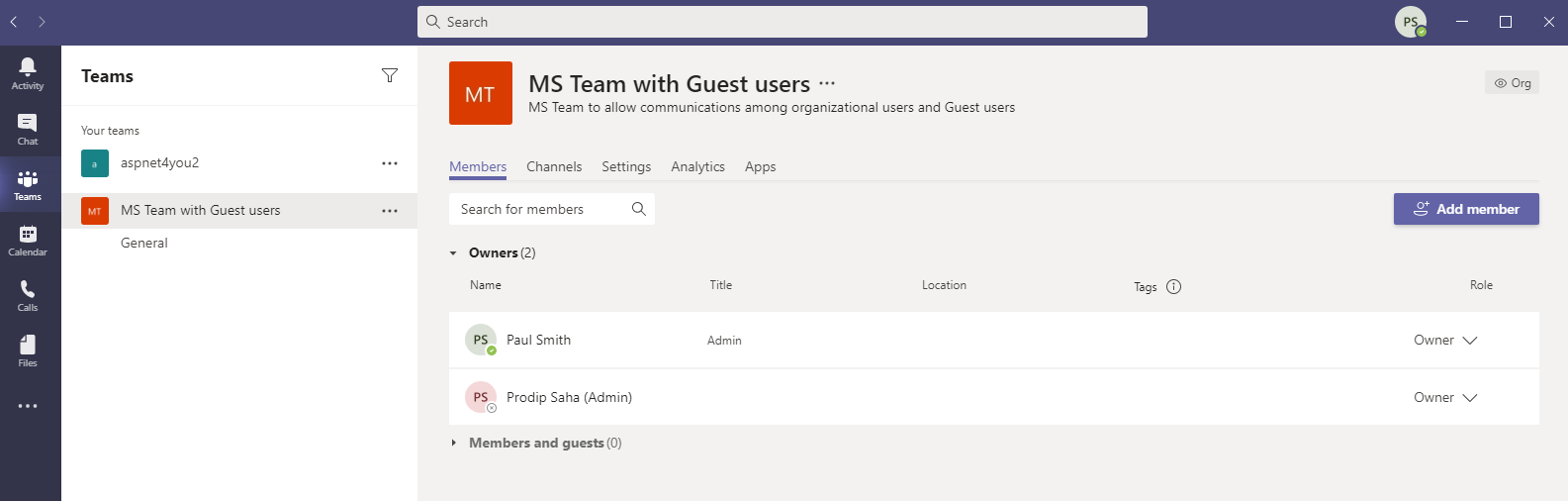
While Paul Smith can invite guests directly from Teams but Paul will not do so because we want to follow the governance process as defined in Identity Governance package. Paul will send emails to the guest users listed in test strategy and have the guest user make the access request. This way access request is fully documented and we can produce audit trails including guest user’s sworn acknowledgement.
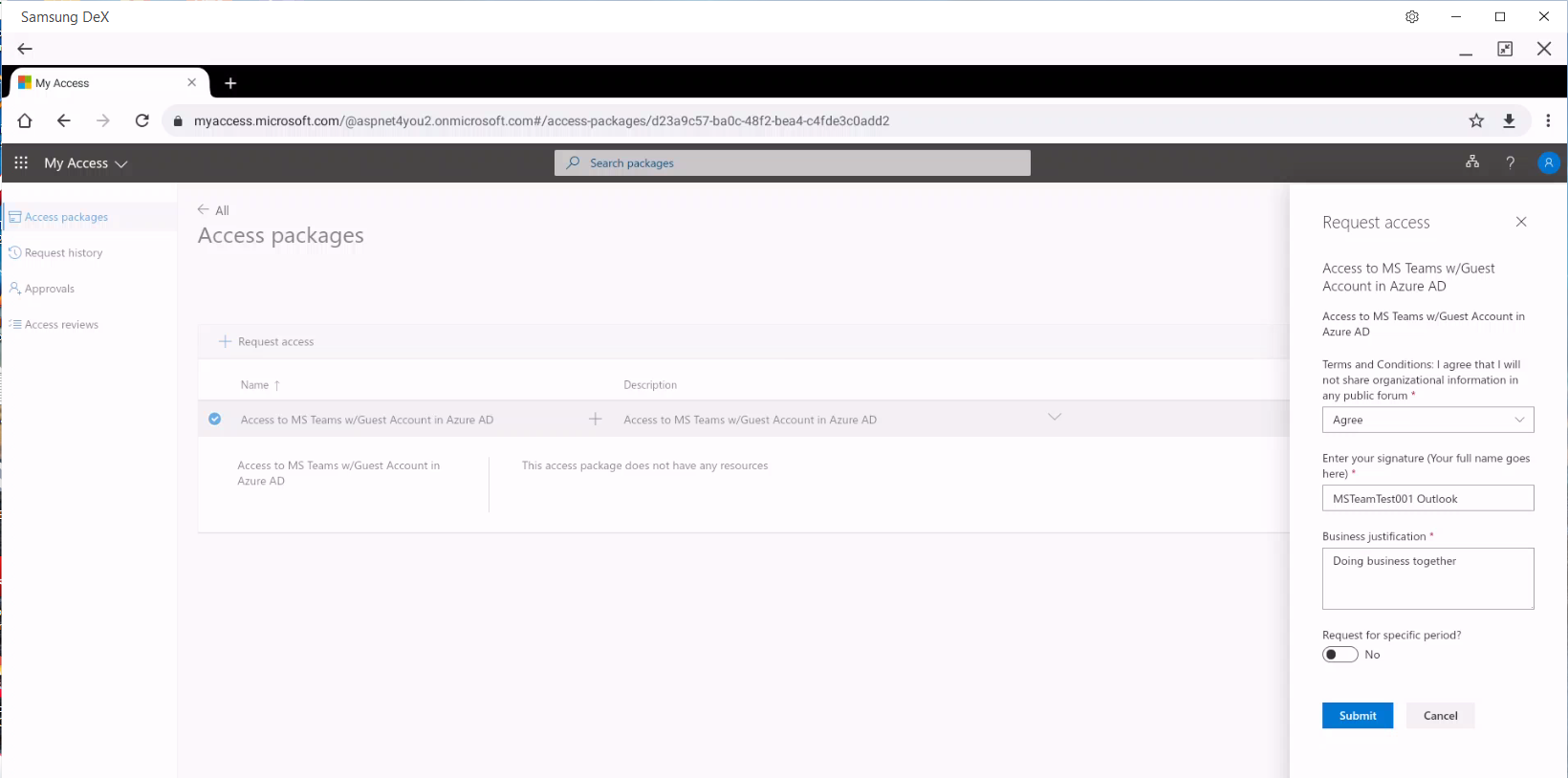
MSTeamTest001@outlook.com requesting guest access using the access package url. MSTeamTest001@outlook.com had to login using username and password. MFA was prompted by Conditional Access policy and it was satisfied. Below is the screenshot of guest access request- user MSTeamTest001@outlook.com must complete all the questions before submitting the request. I am using my Samsung Note 10+ which is displayed with DeX on my desktop. You can use Incognito browser session to switch security context.
MSTeamTest001@aspnet4you.com requesting guest access. This request is made from an incognito browser session.
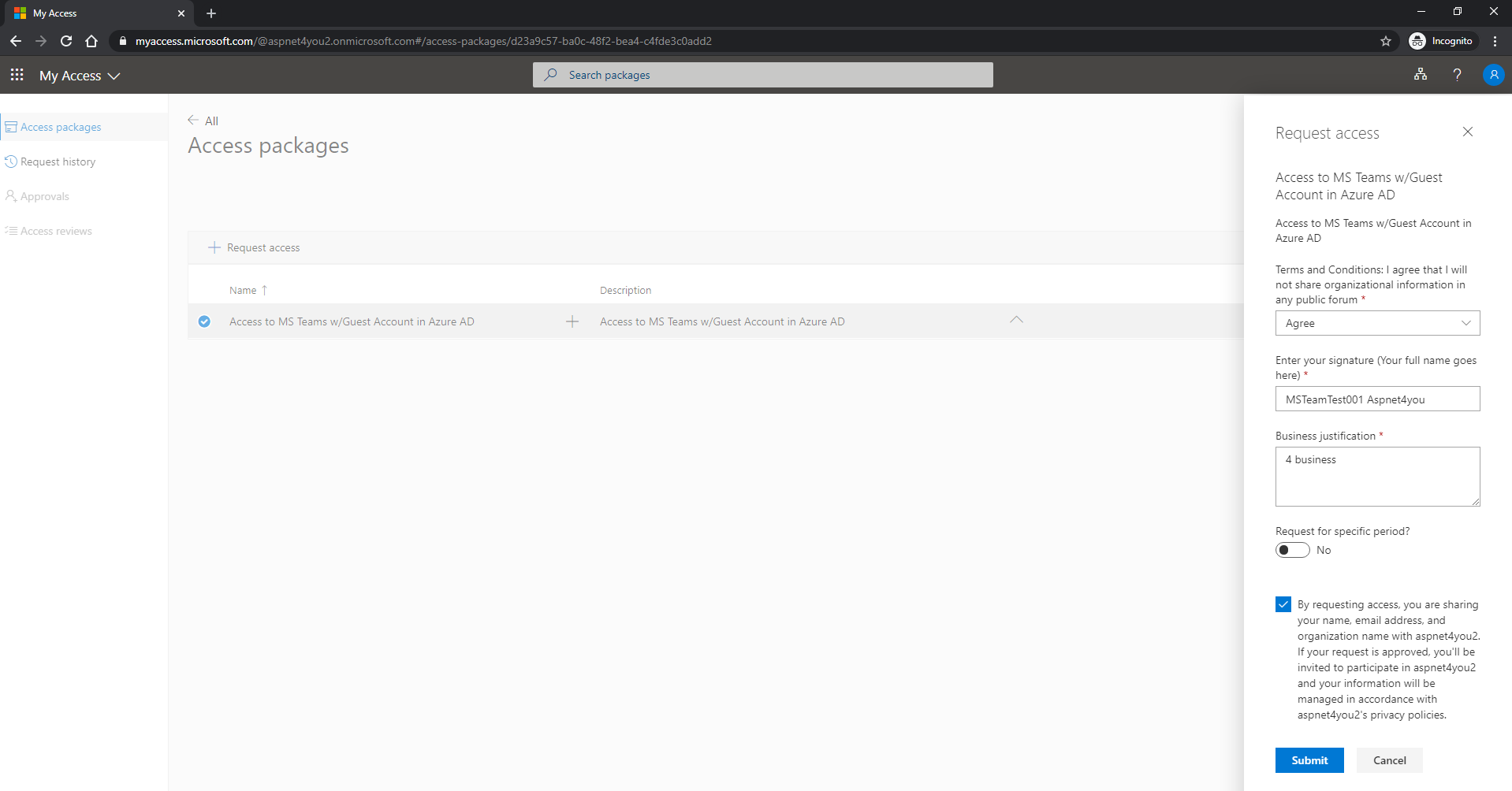
MSTeamTest001@gmail.com- Gmail is not Microsoft account. So, it needs to register with Microsoft Azure AD. MSTeamTest001@gmail.com complied and completed the guest request.
Similarly, MSTeamTest001@aspnet4you.com, happened to be registered with another Azure AD organization, completed the access request.
As mentioned earlier, MSTeamTest002@gmail.com did not register with Azure AD and it can’t sign-in. We are going to leave it there just to complete the negative test. This user can’t request guest access and this user can’t access MS Teams.
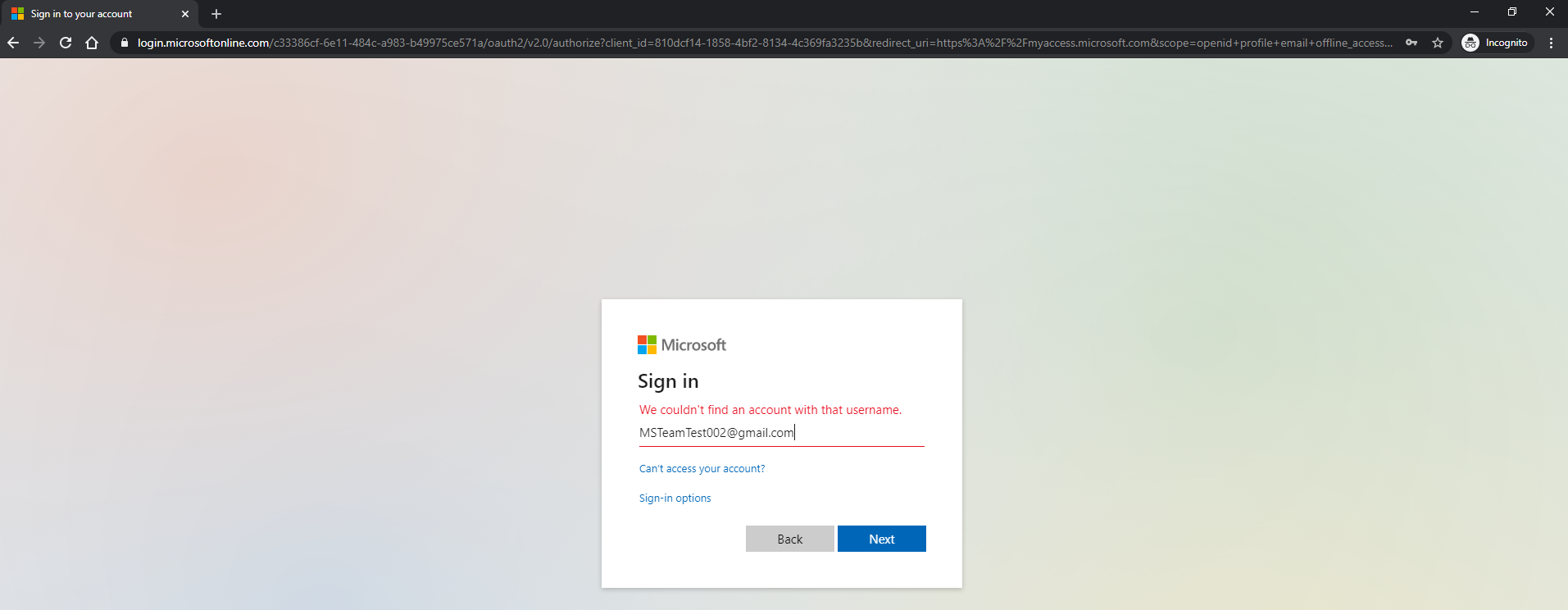
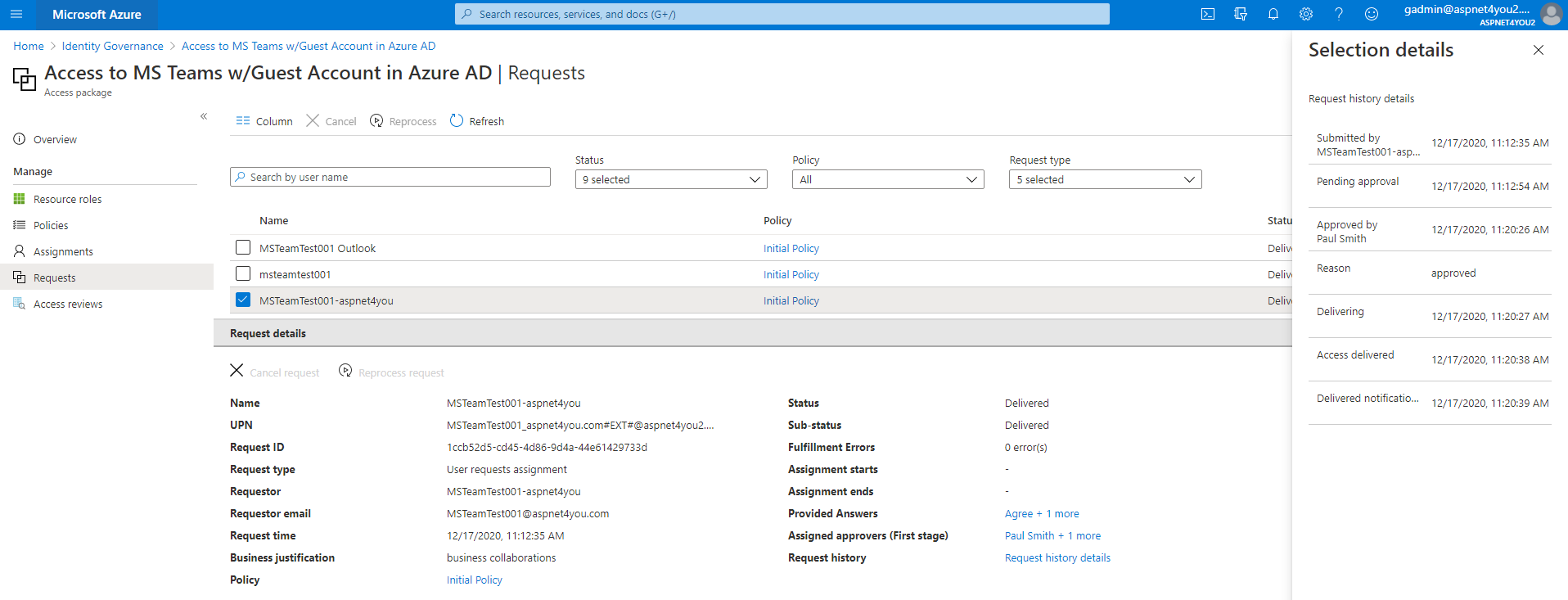
Paul Smith is the approver as defined in the access package. Paul will receive emails to approve the access request. Paul can click the link in the email and approve them on portal. Paul can login to myaccess.microsoft.com and approve the request there. Paul went to myaccess.microsoft.com and approved all the requests at once. Request can be approved individually after checking users complied with the questions in the submission.
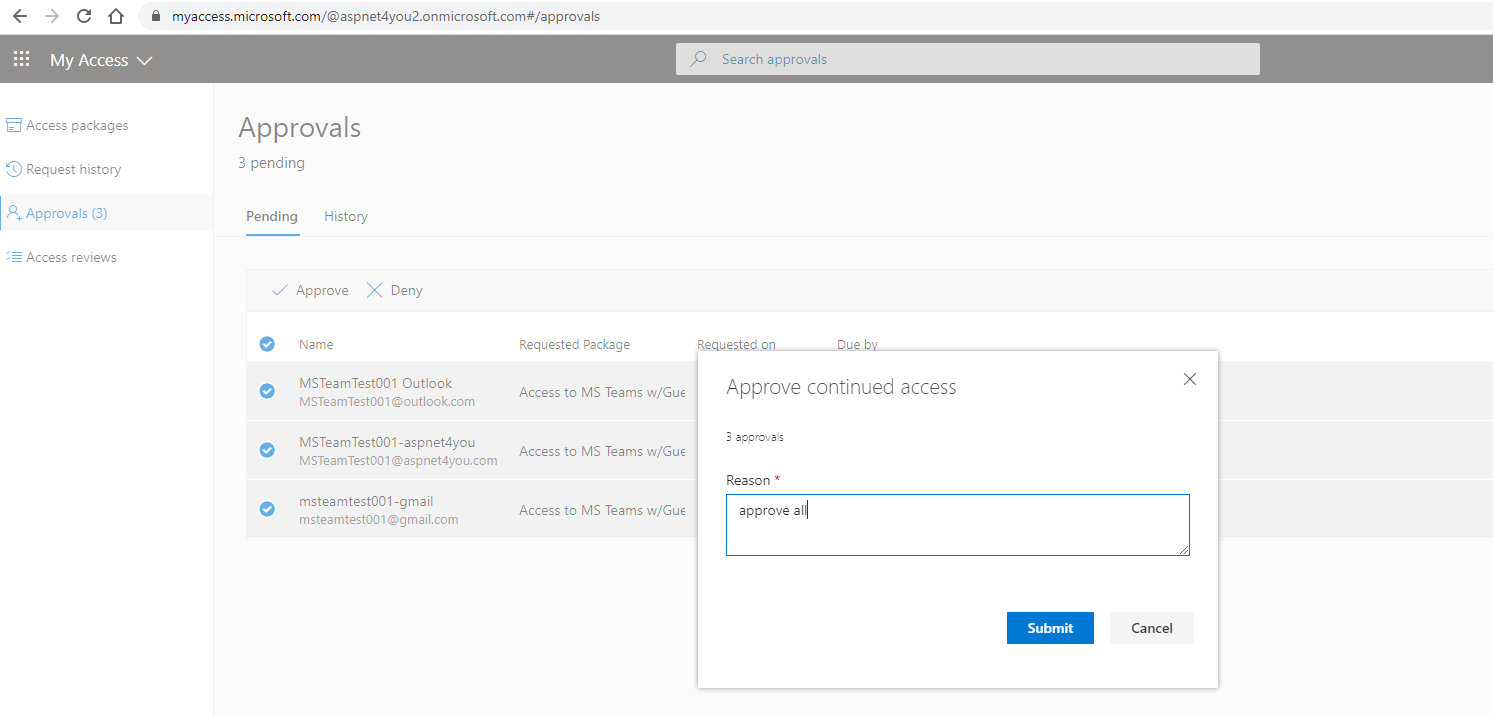
As Global Admin, I can see Paul approved the requests and they are with status- delivered. That means users are created in Azure AD as guest type.
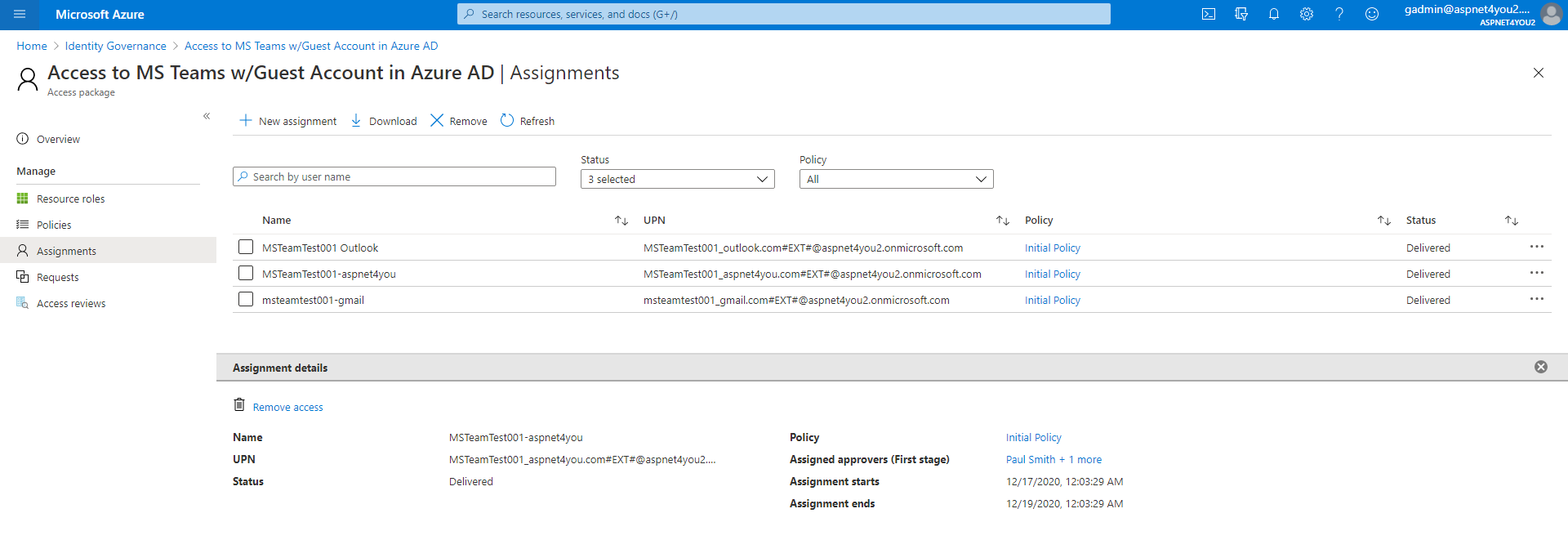
Guest users are active in Azure AD and creating type is Invitation-
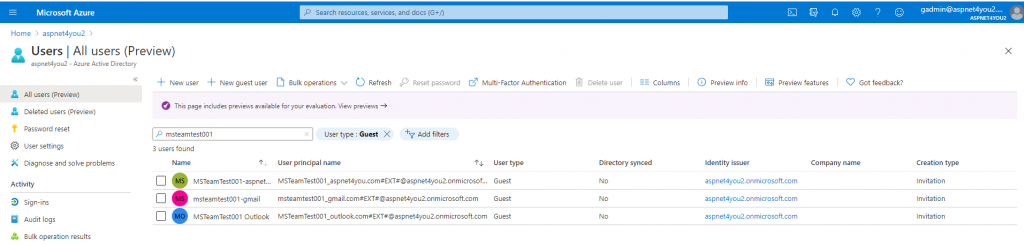
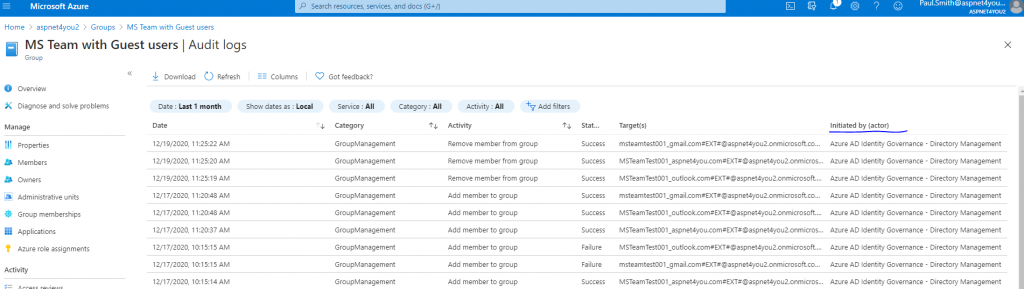
As per resource assignment in access package, guest users are added to the AD group (MS Team with Guest users)-
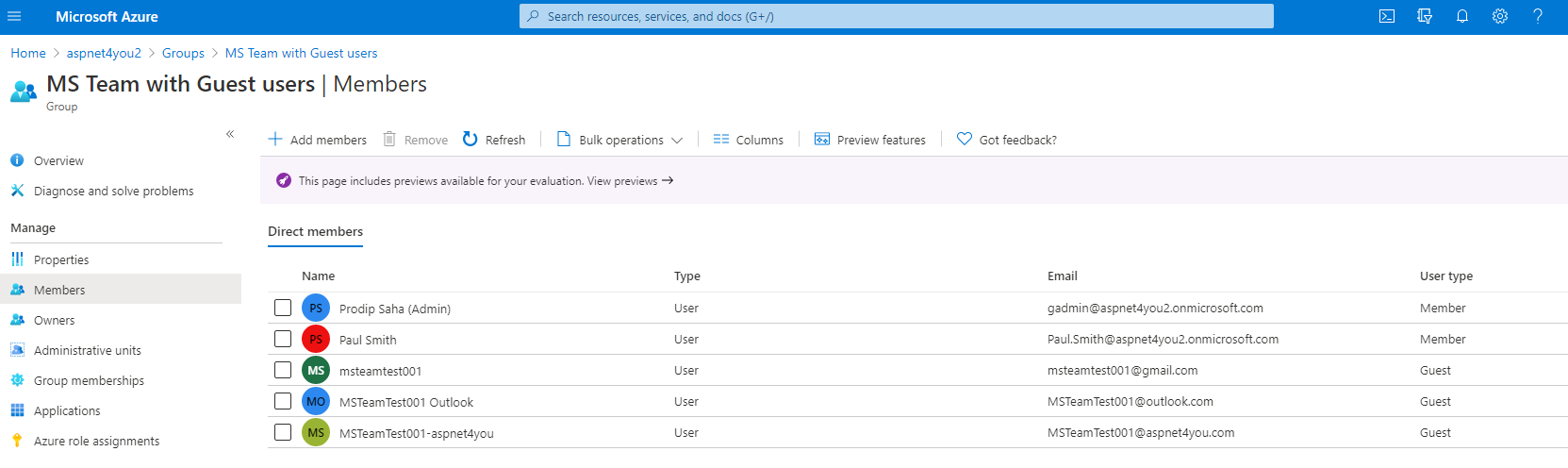
So far testing is going as planned. Guest users are auto onboarded with correct group assignment. However, guest users have to do one more thing. They have to accept or consent the permissions required by our organization (aspnet4you2). To do so, guest user will have to login to myaccess.microsoft.com (i.e. https://myaccess.microsoft.com/@aspnet4you2.onmicrosoft.com#/access-packages/d23a9c57-ba0c-48f2-bea4-c4fde3c0add2). On successful username and password authentication, user will be prompted to accept the permissions.
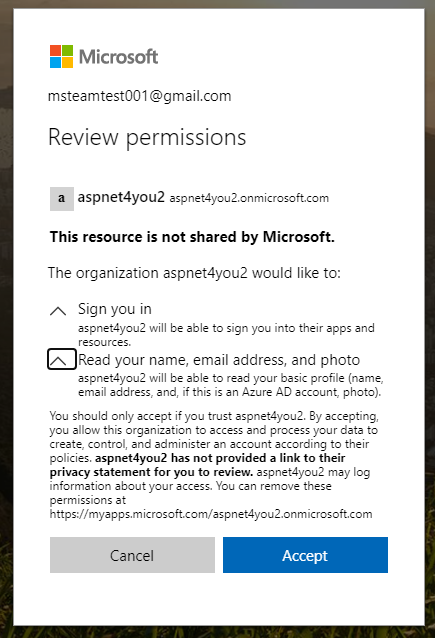
Remember, we are enforcing MFA on guest login? Azure will prompt the user for additional information.
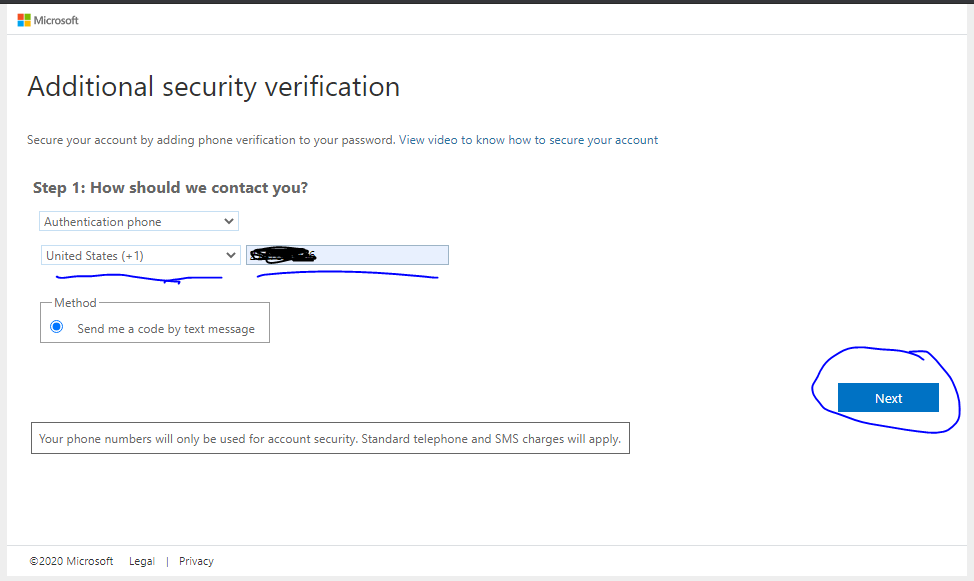
As you click next, additional verification screen will ask for authentication method. I selected phone and provided a mobile number.
Once verification is done, guest user can see their request has been approved and they are part (member) of a team. This assignment is done by the setting defined in Identity Governance Access Package where Resource Role is added.
Okay, all three guest invitees completed the acceptance form and completed their first MFA. They are ready to login to MS Teams app. We are going to use MSTeamTest001@gmail.com to login to Teams app first. After successful authentication, user will be asked to select the organization (when the account has access to multiple organizations). User will be asked to re-authenticate and satisfy MFA and this is enforced by conditional access policy. Little noise for guest user but we need to have proper security controls!
Good news! Guest can exchange messages among them. I happened to logged in to Team on desktop as msteamtest001@gmail.com. I am logged in to Teams mobile with multiple accounts and switching the security context for testing.
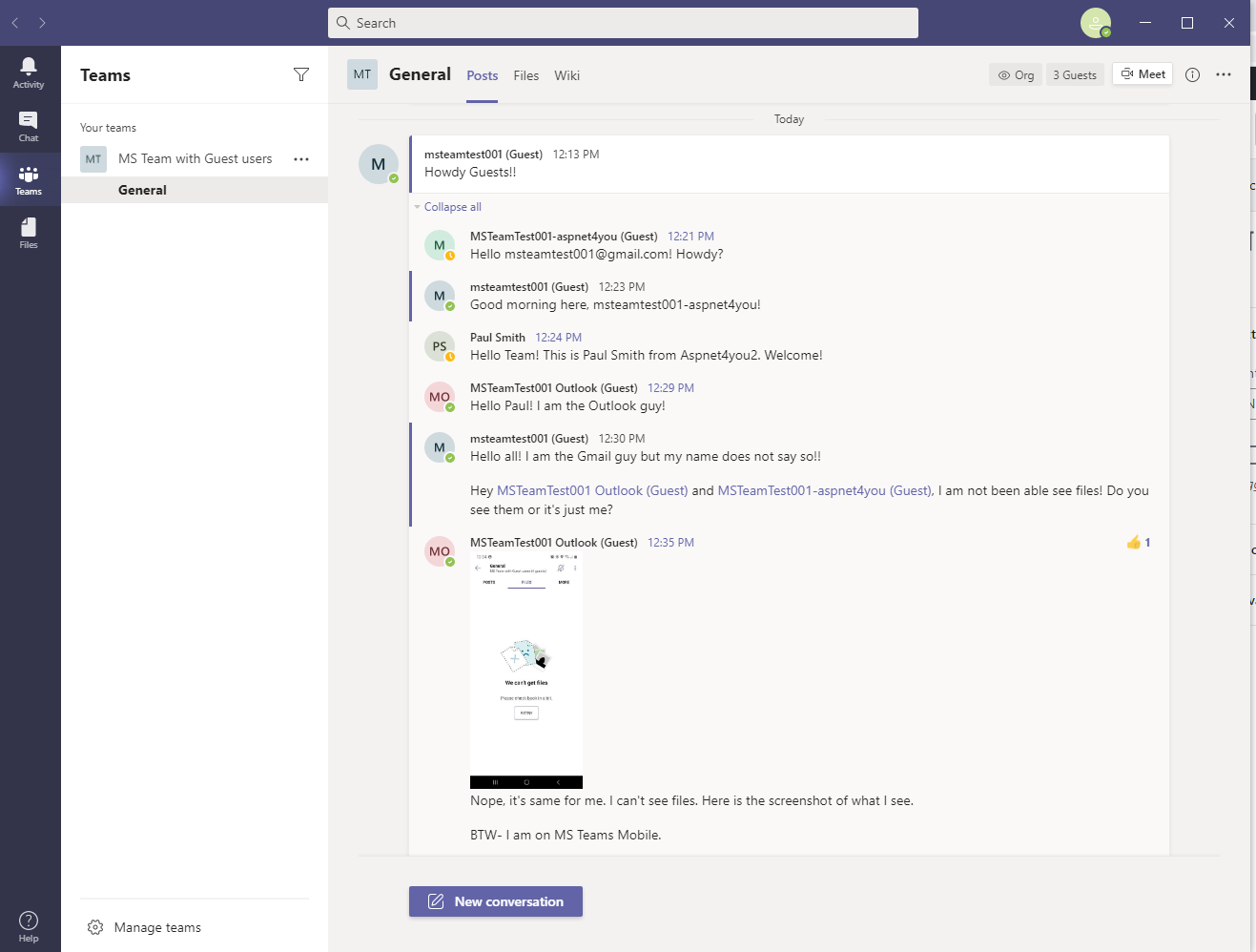
As you can see guest users are complaining that they can’t see files but they can exchange messages. That’s by design. We are restricting guest users from accessing files which are stored in underlying SharePoint site.
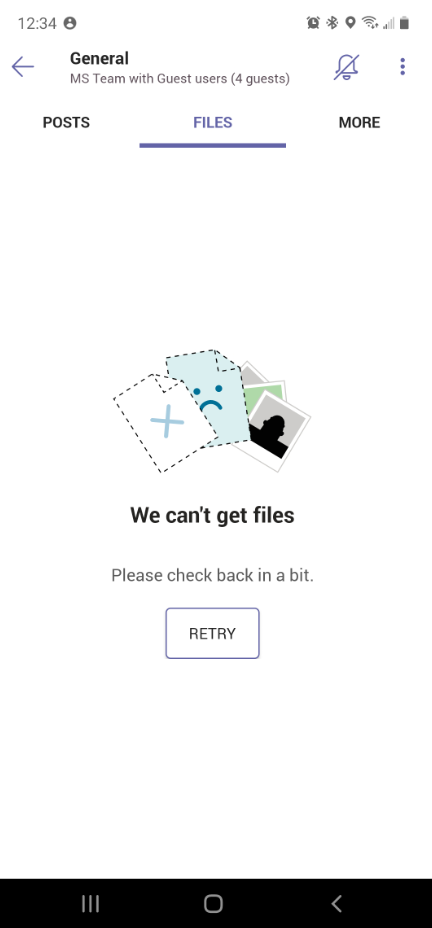
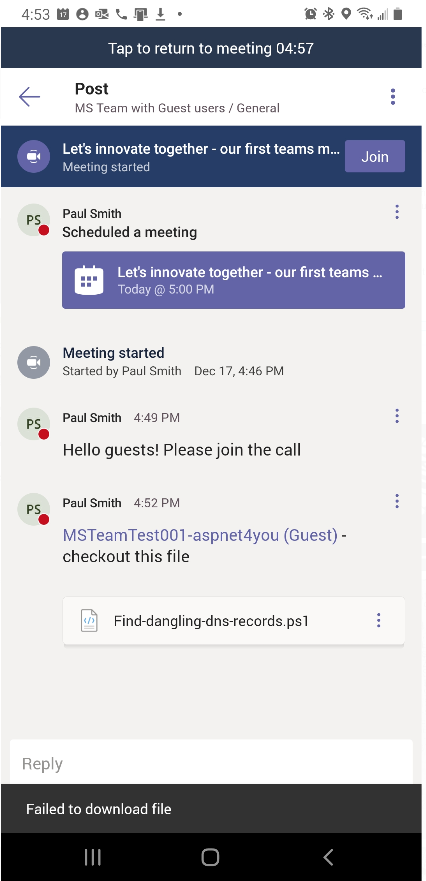
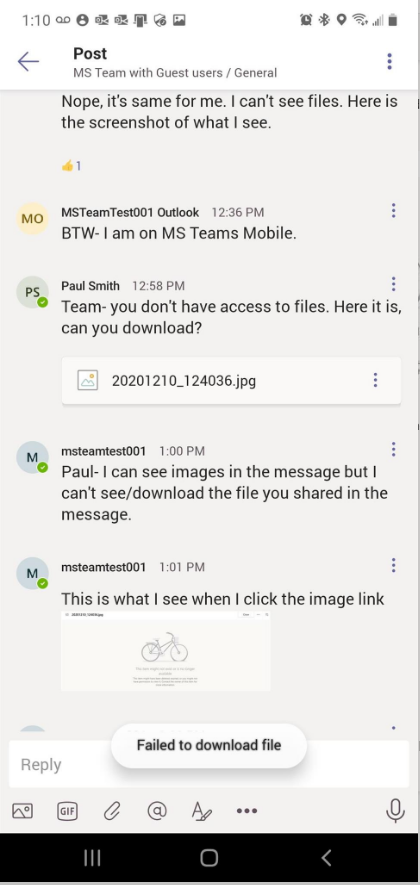
This is what Paul said, “Team- you don’t have access to files. Here is it, can you download?” Guess what? Guest users can’t see the file shared in messages when shared as file. Guest can’t download the file either. They get notification saying, “The file didn’t download”!
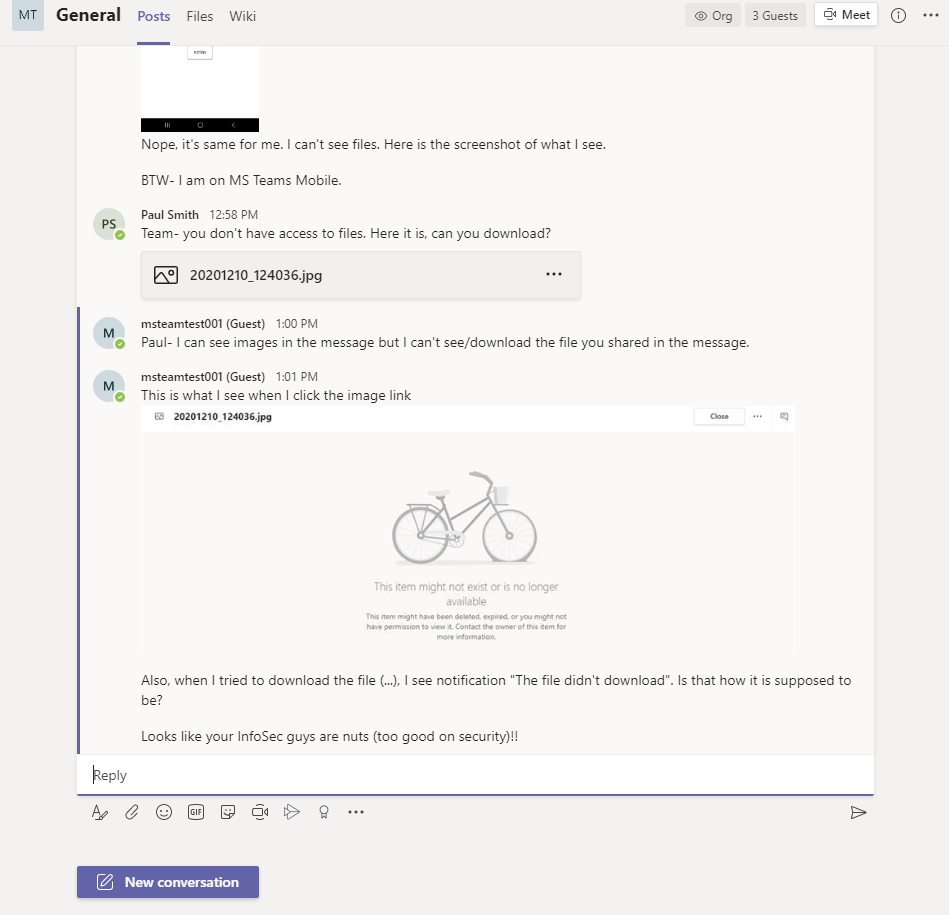
Same complain from msteamtest001@aspnet4you.com! Can’t download the file shared by Paul.
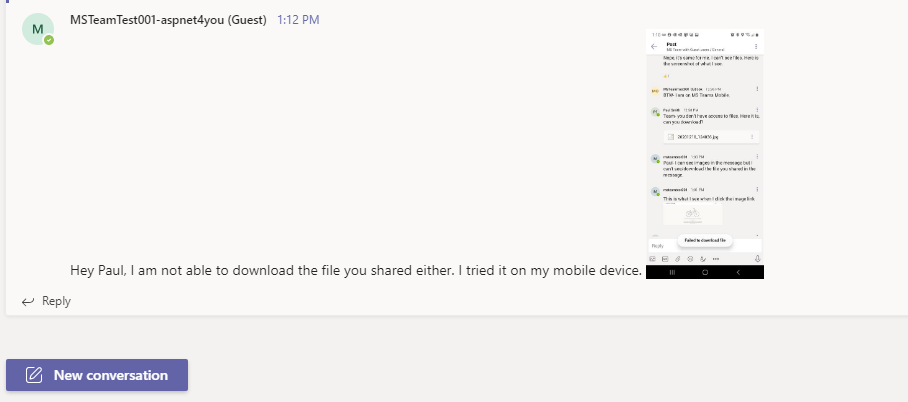
More details from msteamtest001@aspnet4you.com. Guest can see screenshots but they can’t view/download files.
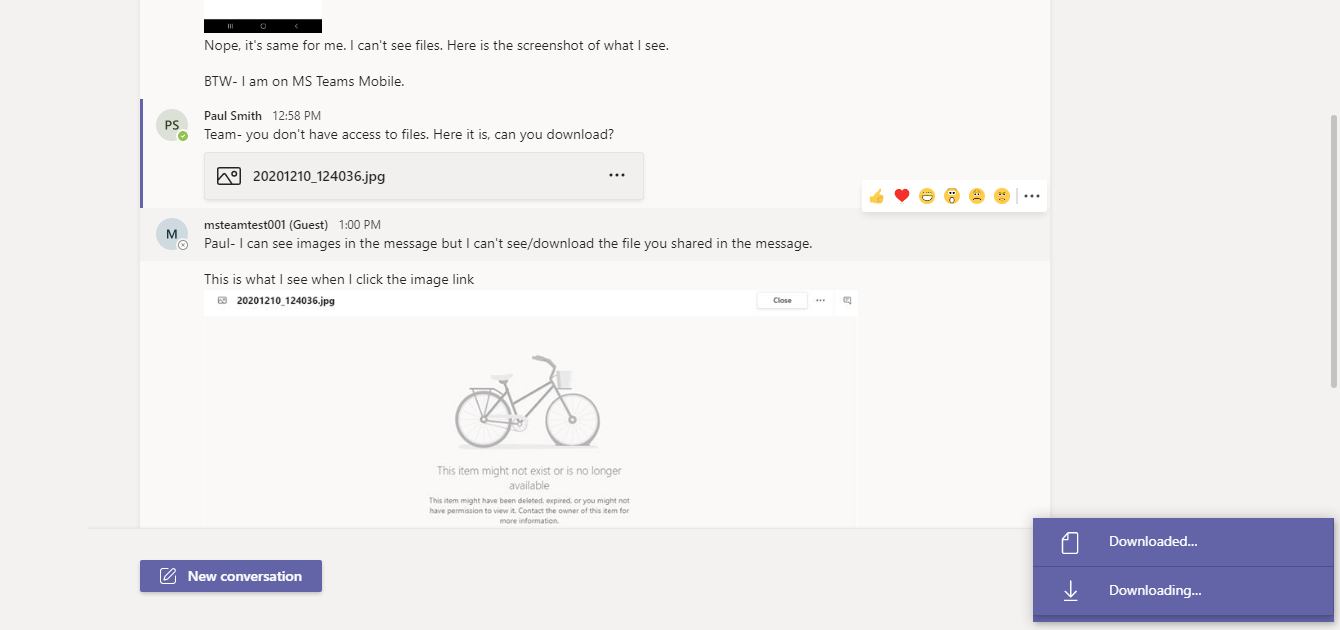
Paul Smith is a member of aspnet4you2 organization and Paul should be able to see/download the file. I am going to login to Teams as Paul and he CAN. Nice greenhouse, BTW!

Okay, we can do more testing but I think we covered our requirements. Let’s take a break and get ready to test MS Teams meetings experience for the guests.
Back from the break! Paul Smith just sent a meeting invite to all the guests for them to join the meeting. MSTeamTest001@aspnet4you.com joined the meeting. Paul shared a file in meeting chat but MSTeamTest001@aspnet4you.com can’t view or download.
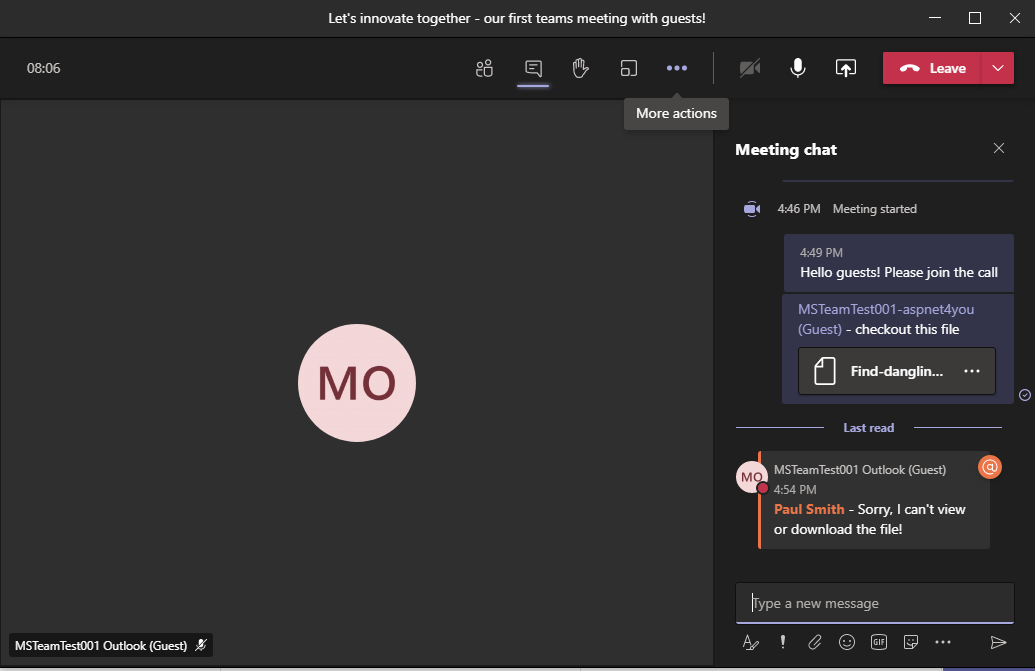
Screenshot sent by MSTeamTest001@aspnet4you.com from his mobile device. Can’t open or download the file shared by Paul.
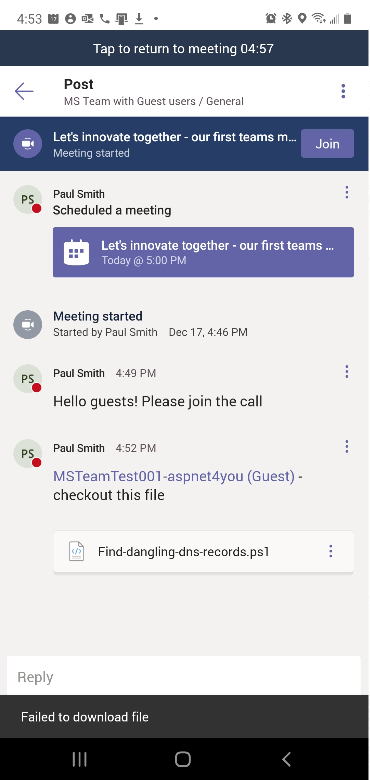
Let’s test if guest ( MSTeamTest001@aspnet4you.com) can share or present screen in the meeting. Good news, guest can present/share screen in the meeting.
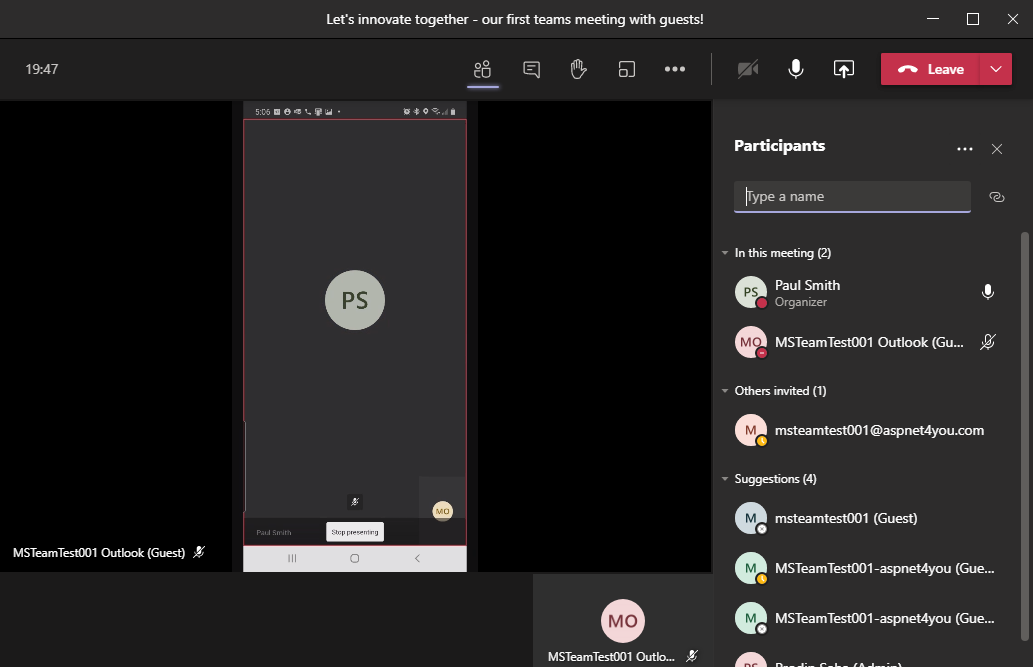
Guest ( MSTeamTest001@aspnet4you.com) can share video as well. I just captured a screenshot of Paul Smith’s team meeting!
As far as the business requirements concern, we accomplished our objectives and requirements are fulfilled. Let’s hold your excitements, we have to look at non-functional and InfoSec requirements!
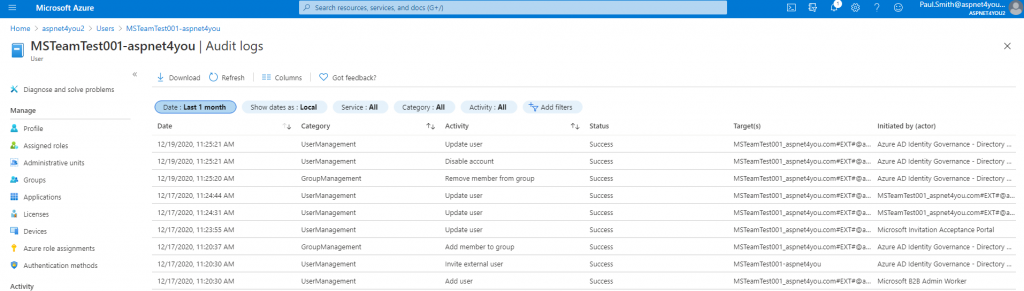
Prodip, the IT Director of Aspnet4you2, got a call from internal auditor Susan. Susan wants to know how guest users got added, who added, who approved and all those audit questions! Relax Susan, the Director said, we have all those audit logs. We can produce who requested guest access and if they agreed to our terms. We know who approved the access request and what resource guest can access. Get your coffee while I gather those logs!
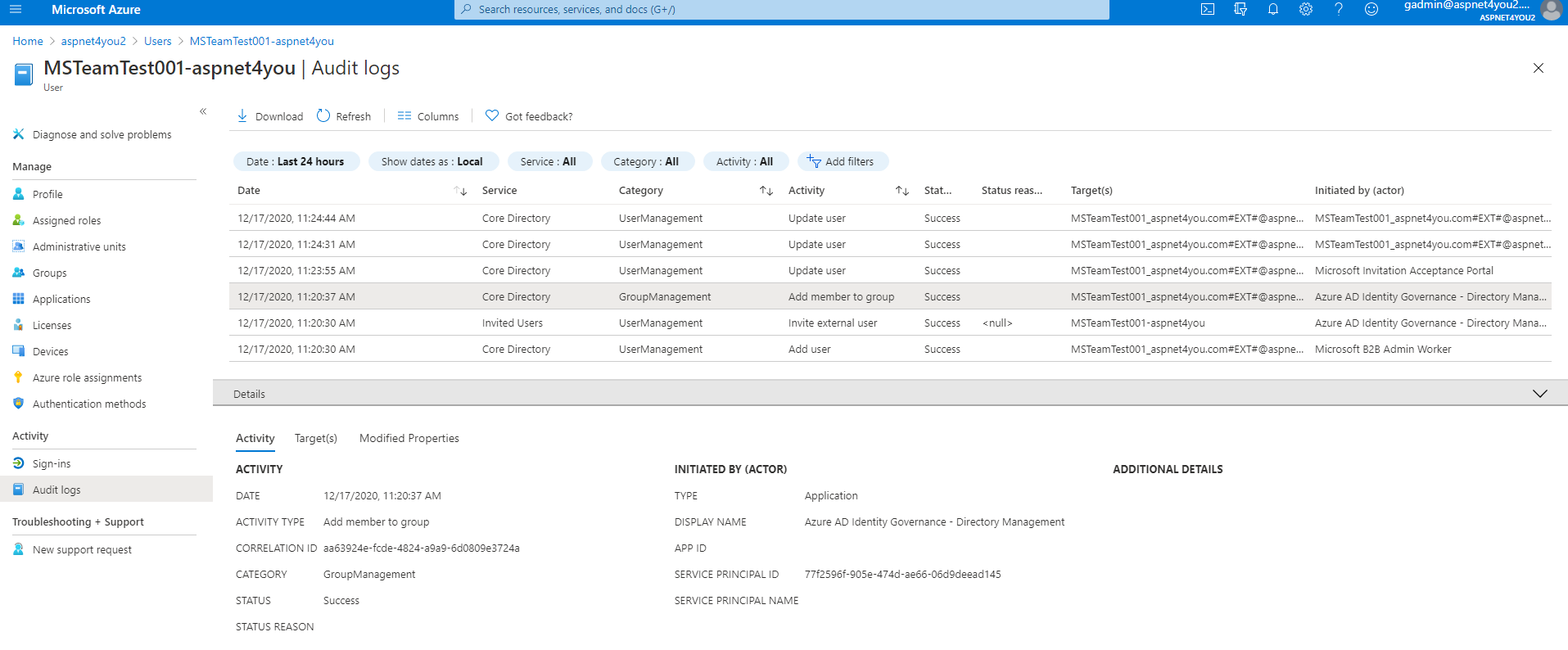
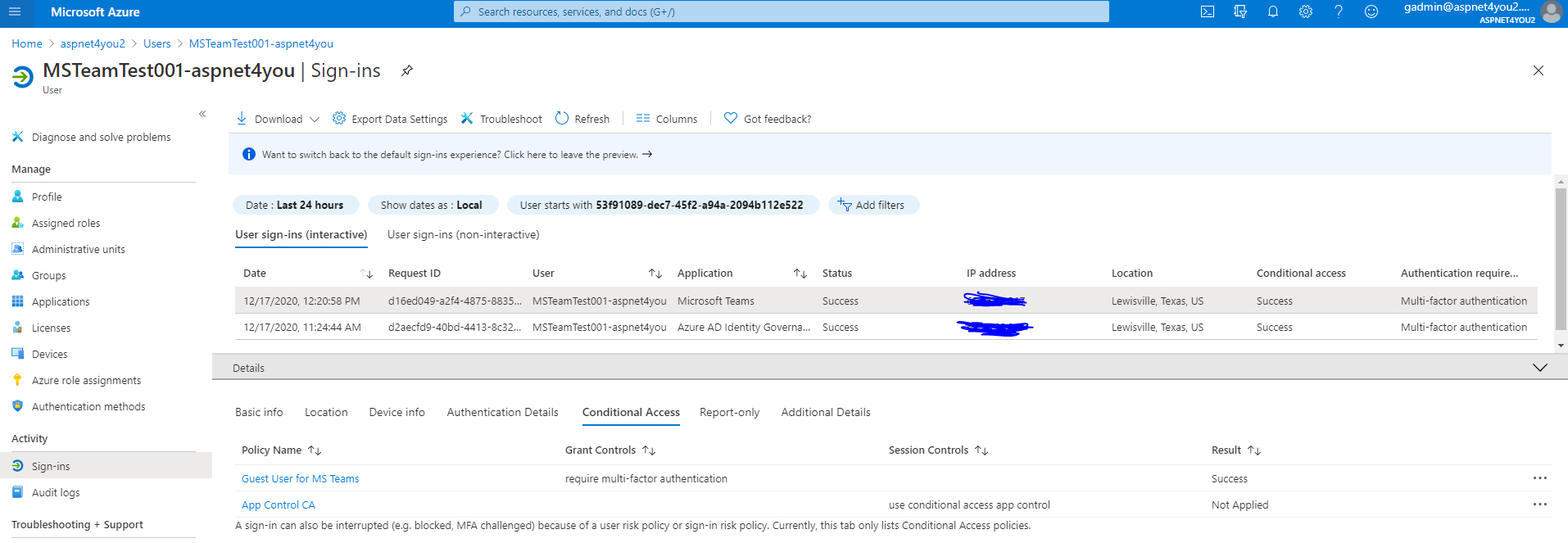
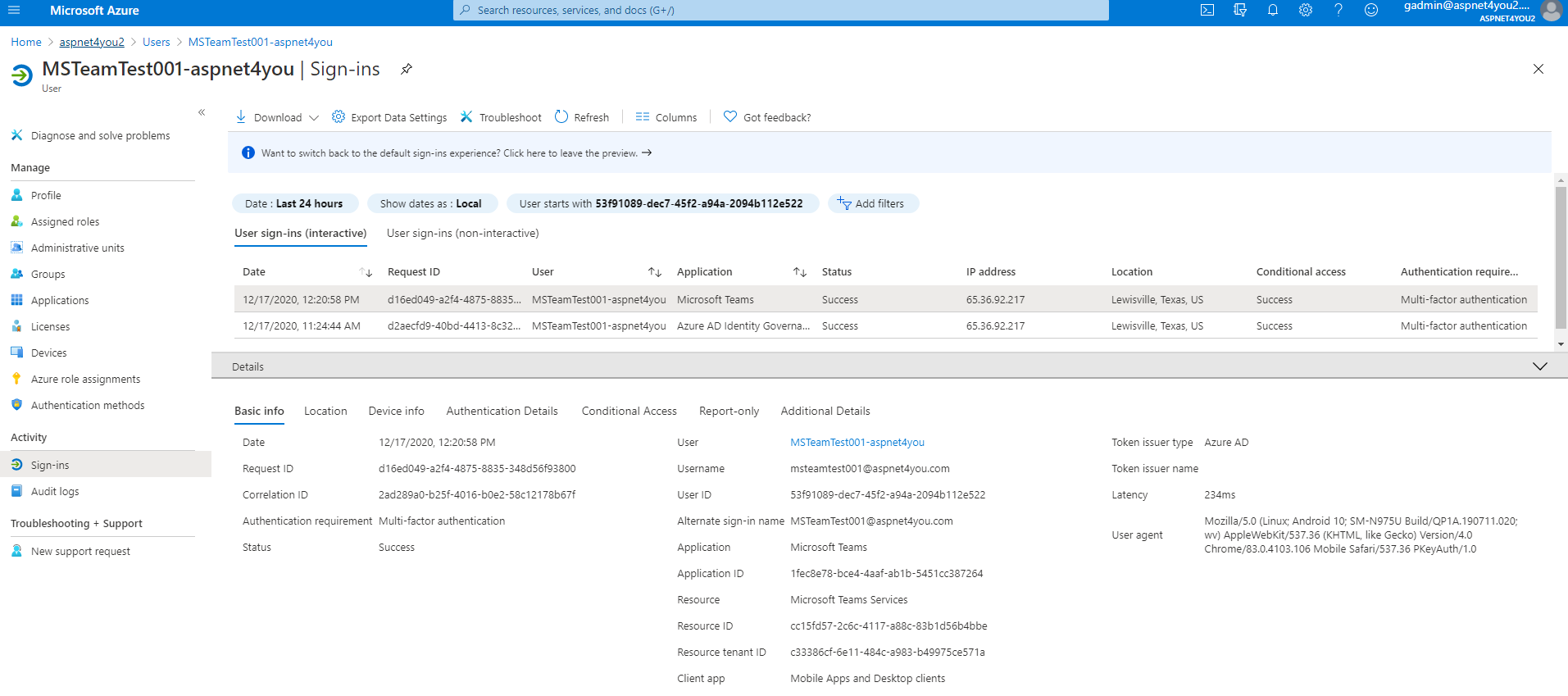
Susan, the auditor, is happy to see the logs. It’s good to see those logs on-demand but we have to send those logs to a storage for long time (365 days) retention for incident response (if ever needed). Azure Log Analytics can be a low cost alternative and you can send the same logs to you choice of SIEM via Azure EventHubs.
As per access package policy, guest user assignment will expire in two (2) days. What would happen is, guest user account will be automatically blocked for sign-in in Azure AD. Azure Identity Governance background job will make it happen. No human interaction is required. Guest account will remain in Azure AD but user would not be able to login.
One of the final part is access review. Paul Smith is assigned as reviewer. We will let Paul start the review after couple of days when user account is blocked for singing.
As per Identity Governance policy, guest user received their account access is ended.
Guess access was allowed for 2 days and Identity Governance locked the account for sign-in and removed the guest users from AD group (assigned as per policy). No manual action required!