Recently, I started a poll on LinkedIn asking experts to vote on egress to internet from Azure vNET, and among the options are –
- Must use proxy or traffic to internet dies
- Use default route (0.0.0.0/0)
- BGP Route Propagation from on-premise
- Use User Defined Routes (UDR)
Those of you who answered the poll- thank you so much for your contribution. Risk tolerance varies from companies to companies. Some companies may prioritize operational convenience while others look for security best practice. You would opt for security best practice if you are with financial organizations.
Hope world is perfect and all traffic can use http/s proxy but that’s never going to happen. For security best practice, all traffic should go through proxy (HTTP/S). What happens when protocol is not HTTP/S? What would happen to the traffic with UDP and TCP (non http) protocol? While these exception traffic can’t go through HTTP proxy, it is mandatory that all traffic must pass through a firewall first. Firewall provides the visibility to all traffic and we can control (allow/deny) the traffic based on FQDN or IP. You comply with preventive and detective controls.
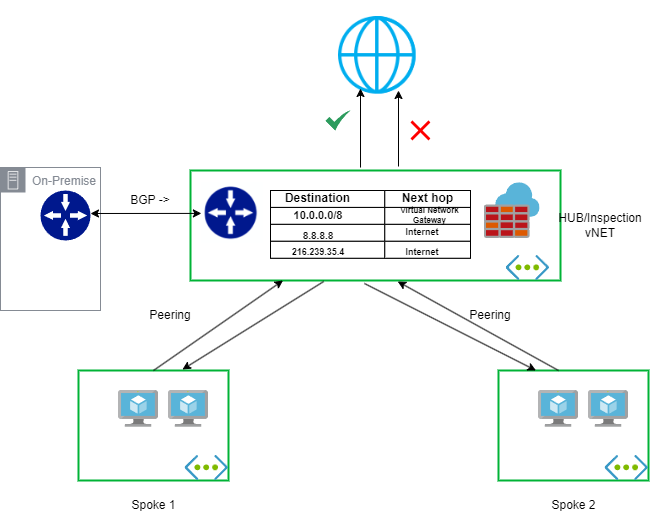
How would you route the traffic to internet once it is approved in firewall by FQDN/IP? Easy way to do this is, by adding default route which is quad zero (0.0.0.0/0) to internet. You never have to manage any routes and it makes the operation simple and easy but it comes with significant risk.
You might ask, do you not trust the firewall and it’s policies? Why not use 0.0.0.0/0 default route to internet once traffic is allowed by firewall?
The short answer is, yes, we do trust the firewall. However, for security best practice, it would be best to add another layer of control after the firewall which is Routes. After all, security is all about defense in depth. Only allow traffic to internet with explicit routes. If firewall admin makes a logical mistake and allow traffic to internet, it would not go out since explicit route is required.
Challenge is, how do you manage those dozens and hundreds of routes? Good news is, you can propagate BGP routes from on-premise to AzureFirewallSubnet. To top it off, we can add custom UDR to the route table and egress to internet directly from Azure.
In summary –
- Always route the traffic to internet over http/s proxy. That’s the rule of the game. Anyone can’t follow the rule are considered exception.
- In addition to firewall, use BGP + UDR in the route table to explicitly route the traffic to internet for exceptional use cases – based on the risk tolerance.
- If there are multiple ip addresses resolve to FQDN and they are dynamic, we don’t have a way to add explicit routes and those traffic can’t go out!
Comments are disabled at the blogs to avoid spams. If you have any feedbacks or comments, you are welcome to contact me over LinkedIn.
